James recently received a secret message from Martha containing an order for custom services. He would like to be able to prove that Martha sent the message and that is could not be forged. What cryptographic goal is James attempting to achieve?
a. Confidentiality
b. Nonrepudiation
c. Security though obscurity
d. Integrity
e. Authentication
Answer: b. Nonrepudiation
You might also like to view...
____ are used by programs on the Internet (remote) and on a user's computer (local) to confirm the user's identity to any third party concerned.?
A. ?Symmetric keys B. ?Symmetric encryption algorithms C. ?Digital signatures D. ?SMTP and IMAP
Supporters of neutral locations for interviews believe that it _____.
A. makes the interviewee feel comfortable during the meeting B. gives the interviewee easy access to supporting material that might be needed C. keeps interruptions to a minimum so people can concentrate fully D. gives the interviewee an opportunity to take calls during the interview
A(n) __________________ gives a router the actual instructions telling it what to do with incoming packets and where to send them.
Fill in the blank(s) with the appropriate word(s).
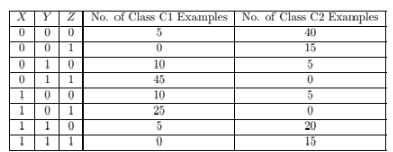
Compute a two-level decision tree using the greedy approach described in this chapter. Use the classification error rate as the criterion for splitting. What is the overall error rate of the induced tree?
Consider the following set of training examples.