____________________ access does not restrict a class's internal access to its own members.
Fill in the blank(s) with the appropriate word(s).
Private
You might also like to view...
Create a new version of the lineDetect function that takes in a threshold and create a movie using lineDetect where the threshold changes depending on the frame number.
What will be an ideal response?
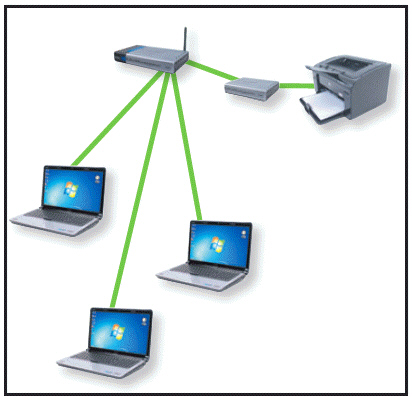 The accompanying figure shows the ____ method of connecting a printer to a network.
The accompanying figure shows the ____ method of connecting a printer to a network.
A. one-computer B. direct-to-router C. print-server D. direct-to-printer
The md5sum and sha1sum commands generate a checksum used to verify ____________________.
Fill in the blank(s) with the appropriate word(s).
____ is the process of transmitting all the files that constitute your website from your computer to the top directory, also called the root folder on the selected server or host computer.
A. Downloading B. Publishing C. Transferring D. Hosting