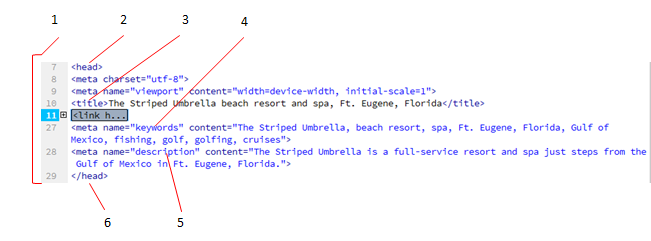
Item ____ in the figure above is the opening head tag.
A. 1
B. 2
C. 5
D. 6
Answer: B
You might also like to view...
Case-Based Critical Thinking QuestionsCase 9-1Kyra is preparing speaker notes and handouts for her presentation. Please answer the questions below.To print speaker notes, Kyra clicks the ______ tab, then clicks Print
A. HOME B. FILE C. REVIEW D. OUTPUT
From the following, select the item that makes this statement FALSE. When performing a continuity check on a cable _______
A) Not all pins are wired to the matching pin on the other end. B) Not all pins have to be connected to a pin on the other end. C) All pins connect one to one. D) A 0 ohm reading means a good connection.
A wireless access point connects to the wired network. What can you do to prevent unauthorized users from accessing shared files on the wired network?
A) Disable SSID broadcasting on the access point. B) Enable WEP, TKIP, or AES on the access point. C) Configure NTFS permissions on the shares. D) Install a firewall for the networks.
Tables with a many-to-many relationship must be related to an additional table, called a(n) ____________________ table.
Fill in the blank(s) with the appropriate word(s).