Provide steps in encrypting messages with openSSL.
OpenSSL can be used as a standalone tool for encryption. While many encryption algorithms can be
used, this lab focuses on AES. To use AES to encrypt a text file directly from the command line using
OpenSSL, follow the steps below:
Encrypting a Text File
a. Log into the CyberOps Workstation VM.
b. Open a terminal window.
c. Because the text file to be encrypted is in the /home/analyst/lab.support.files/ direc-
tory, change to that directory:
```
[analyst@secOps ~]$ cd /home/analyst/lab.support.files/
[analyst@secOps lab.support.files]$
```
d. Type the command below to list the contents of the encrypted letter_to_grandma.txt
text file on the screen:
```
[analyst@secOps lab.support.files]$ cat letter_to_grandma.txt
Hi Grandma,
I am writing this letter to thank you for the chocolate chip cookies you sent
me. I got them this morning and I have already eaten half of the box! They are
absolutely delicious!
I wish you all the best. Love,
Your cookie-eater grandchild.
[analyst@secOps lab.support.files]$
```
e. From the same terminal window, issue the command below to encrypt the text file. The
command will use AES-256 to encrypt the text file and save the encrypted version as
message.enc. OpenSSL will ask for a password and for password confirmation. Provide
the password as requested and be sure to remember the password.
```
[analyst@secOps lab.support.files]$ openssl aes-256-cbc -in letter_to_grandma.
txt -out message.enc
enter aes-256-cbc encryption password:
Verifying - enter aes-256-cbc encryption password:
[analyst@secOps lab.support.files]$
```
f. When the process is finished, use the cat command again to display the contents of the
message.enc file.
[analyst@secOps lab.support.files]$ cat message.enc
Did the contents of the message.enc file display correctly? What does it look like?
Explain.
No. The file seems broken as just symbols are displayed. The symbols are shown
because OpenSSL has generated a binary file.
g. To make the file readable, run the OpenSSL command again, but this time add the -a
option. The -a option tells OpenSSL to encode the encrypted message as Base64 before
storing the results in a file.
Note: Base64 is a group of similar binary-to-text encoding schemes used to represent binary data in an
ASCII string format.
```
[analyst@secOps lab.support.files]$ openssl aes-256-cbc -a -in letter_to_grand-
ma.txt -out message.enc
enter aes-256-cbc encryption password:
Verifying - enter aes-256-cbc encryption password:
```
h. Once again, use the cat command to display the contents of the, now re-generated,
message.enc file:
Note: The contents of message.enc will vary.
```
[analyst@secOps lab.support.files]$ cat message.enc
U2FsdGVkX19ApWyrn8RD5zNp0RPCuMGZ98wDc26u/vmj1zyDXobGQhm/dDRZasG7
rfnth5Q8NHValEw8vipKGM66dNFyyr9/hJUzCoqhFpRHgNn+Xs5+TOtz/QCPN1bi
08LGTSzOpfkg76XDCk8uPy1hl/+Ng92sM5rgMzLXfEXtaYe5UgwOD42U/U6q73pj
a1ksQrTWsv5mtN7y6mh02Wobo3A1ooHrM7niOwK1a3YKrSp+ZhYzVTrtksWDl6Ci
XMufkv+FOGn+SoEEuh7l4fk0LIPEfGsExVFB4TGdTiZQApRw74rTAZaE/dopaJn0
sJmR3+3C+dmgzZIKEHWsJ2pgLvj2Sme79J/XxwQVNpw=
[analyst@secOps lab.support.files]$
```
Is message.enc displayed correctly now? Explain.
Yes. While message.enc is encrypted, it is now correctly displayed because it has been
converted from binary to text and encoded with Base64.
Can you think of a benefit of having message.enc Base64-encoded?
The encrypted message can now be copied and pasted in an email message, for
example.
You might also like to view...
Answer the following statements true (T) or false (F)
1. All programming languages have math operators that perform arithmetic. 2. The syntax rules dictate how keywords, operators, and various punctuation characters must be used in a program. 3. A programming statement can consist of keywords, operators, punctuation, and other allowable programming elements, arranged in the proper sequence to perform an operation. 4. Because compilers combine translation and execution, they typically do not create separate machine language programs.
FIGURE EX 6-1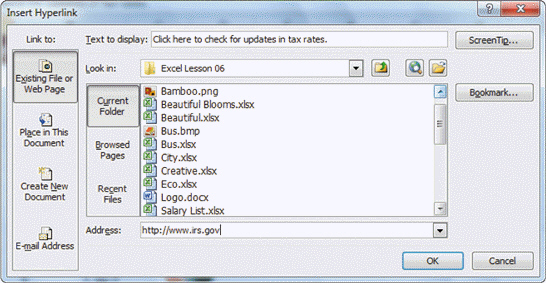 In order to access the Insert Hyperlink dialog box shown in Figure EX 6-1 above, you would ____.
In order to access the Insert Hyperlink dialog box shown in Figure EX 6-1 above, you would ____.
A. Click the cell she wants to use for the hyperlink. On the Insert tab of the Ribbon, in the Links group, click the Hyperlink button. B. Right-click the cell or object, and then click Hyperlink on the shortcut menu C. either a. or b. D. neither a. nor b.
If a child folder is inheriting its permissions from a parent folder, it could be said that the parent is propagating those permissions to the child
Indicate whether the statement is true or false
What are three questions you might want to ask a user when he brings a computer problem to you?
What will be an ideal response?