Trusted macros have been known to add, edit, or remove data from a database and often spread to other databases or even to the user's computer
Indicate whether the statement is true or false
FALSE
Computer Science & Information Technology
You might also like to view...
The system and application security competency has the required functional perspective of ____.
A. manage, design B. manage C. manage, design, evaluate D. manage, evaluate
Computer Science & Information Technology
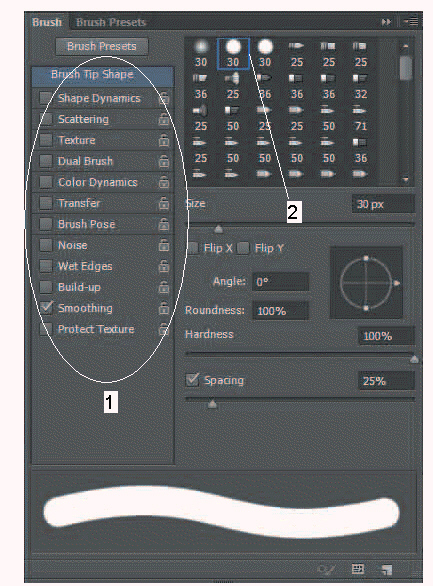 In the accompanying figure, item 1 displays a list of ____.
In the accompanying figure, item 1 displays a list of ____.
A. brush sources B. brush tip options C. brush tip sizes D. brush locations
Computer Science & Information Technology
Every statement in Java ends with ________.
a. a semicolon (;) b. a comma (,) c. a period (.) d. an asterisk (*)
Computer Science & Information Technology
Excel applies ____________________ to cells when specified criteria are met, such as when you apply green, bold formatted text to all sales orders greater than $50,000.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology