Which of the following describes an LDAP injection attack?
A. Creating a copy of user credentials during the LDAP authentication session
B. Manipulating an application's LDAP query to gain or alter access rights
C. Sending buffer overflow to the LDAP query service
D. Using XSS to direct the user to a rogue LDAP server
Answer: B. Manipulating an application's LDAP query to gain or alter access rights
You might also like to view...
What happens if you forget to place a null character in a character array and then write the array using cout?
What will be an ideal response?
Studies have shown that more than 25 percent of all business worksheets have errors.
Answer the following statement true (T) or false (F)
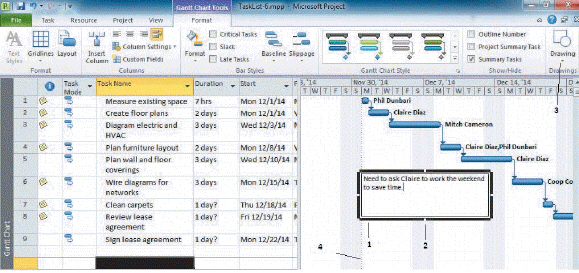 The item marked 1 in the accompanying figure is a ____.
The item marked 1 in the accompanying figure is a ____.
A. Drawing box B. Text box C. Comment box D. None of the above
What are some of the reasons that projects dates and costs get off track? How can a baseline on a current project help with future planning?
What will be an ideal response?