Failure to follow sound scientific procedure when performing internal forensic investigations in the corporate environment can have what kind of impact on the organization?
a. Terminated employees have an additional right to sue.
b. If a case turns into a criminal matter, evidence that was improperly collected or handled may be declared inadmissible, damaging the organization's position.
c. The courts are unlikely to accept any of the evidence you present if even one piece is determined to be suspect.
d. You will have to bring in third-party expert witnesses to corroborate your findings, at your own expense.
b.
You might also like to view...
In this lab, you are configuring OSPF to the adjacent LAN for the network shown in Figure 1. You will be required to verify that computers in your LAN can ping the neighbor LAN. Note that a serial interface is being used to interconnect the LANs. You are configuring routing for both 172.20.15.0 and 192.168.25.0 networks. A subnet mask of 255.255.255.224 is being used. Use 56000 for the clock rate on the serial link (DCE interface). Use a subnet mask of 255.255.255.252 on the serial link connecting the two routers.
Computer IP Addresses, Subnet Masks, and Gateway Addresses
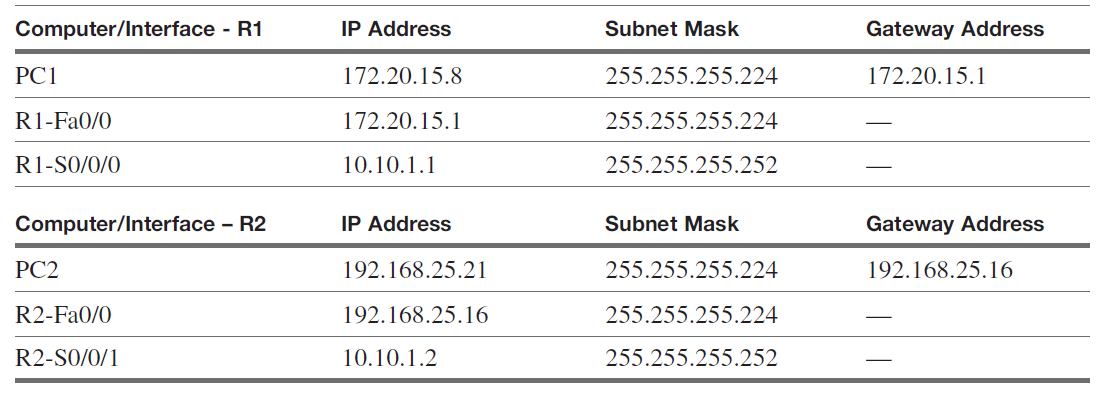
1. Configure the gateway address for FastEthernet 0/0 and the serial s0/0/0 interfaces on
Router R1. You also need to configure the IP address and the gateway address for PC-1.
Use the IP address and subnet mask specified in Table 1. You will need to enable each
interface and set the clock rate on the serial interface to 56000. List the router prompts
and commands used to configure the interfaces.
2. Configure the gateway address for FastEthernet 0/0 and the serial s0/0/1 interfaces on Router R2. Use the IP addresses and subnet masks specified in Table 1. Enable each interface and list the router prompts and commands used to configure the interfaces.
3. Configure the host name for your routers. R1 should be renamed LAN-A, and R2 should be renamed LAN-B. List the router prompts and commands used to configure the router’s host name.
4. The proper commands to verify that the interfaces on the LAN-A and LAN-B routers have b
PowerPoint's ________ removes unwanted portions of a picture so the picture does not appear as a self-contained rectangle
A) Background Removal B) Dotted Edges C) Blur Edges D) Fade Out
After editing sources using the Source Manager, do which of the following to ensure the bibliography reflects the changes?
A) Press the Update Citations and Bibliography button above the bibliography. B) Inspect the document. C) Check the document for spelling and grammar errors. D) Check the document for accessibility.
____ is a block cipher mode in which each possible block of plaintext has a defined corresponding ciphertext value.
A. CBC B. CFB C. OFB D. ECB