A rogue AP can be described as which of the following?
A. an AP whose security settings have not been set
B. an AP designed to mimic an authorized AP
C. an AP that has malfunctioned and allows unauthorized users to access it
D. an unauthorized AP brought into the enterprise network
Answer: D
You might also like to view...
Figure 8.12 shows an example of an EER diagram for a small private airport database that is used to keep track of airplanes, their owners, airport employees, and pilots. From the requirements for this database, the following information was collected: Each airplane has a registration number [Reg#], is of a particular plane type [of_type], and is stored in a particular hangar [stored_in]. Each plane_type has a model number [Model], a capacity [Capacity], and a weight [Weight]. Each hangar has a number [Number], a capacity [Capacity], and a location [Location]. The database also keeps track of the owners of each plane [owns] and the employees who have maintained the plane [maintain]. Each relationship instance in owns relates an airplane to an owner and includes the purchase date [Pdate]. Ea
What will be an ideal response?
Using the P E R T diagram in Figure below determine the answers:
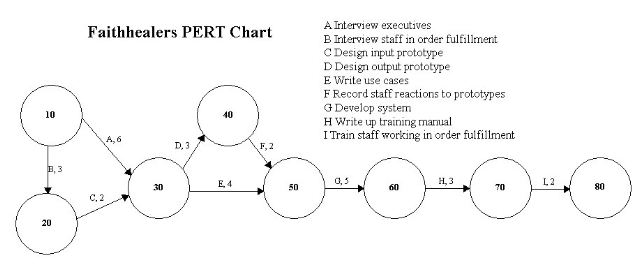
a. What activities can you expedite to complete the project a week ahead of schedule?
b. Suppose Activity E is the least costly activity to expedite. What happens if you try to expedite the project by more than one week? Explain.
_________ are queries nested within another query
A) Union queries B) Find duplicates queries C) Parameter queries D) Subqueries
SongLyricsBook is a(n) ____________________ that finds the lyrics for a song and a YouTube video of an artist performing it.
Fill in the blank(s) with the appropriate word(s).