Describe the main characteristics of buffer overflow attacks for SMTP servers.
What will be an ideal response?
A buffer overflow is one of the main types of attacks on the Internet. Hackers may try to overflow the buffer of the user's system. In this instance, a very long username, password, or file name is sent to the server. By doing this, a hacker may be able to disrupt a running process and insert malicious code to be executed on the server.?Hackers can create a buffer overflow on a system by sending a long HELO command, long e-mail names in MAIL or RCPT commands, or a long command. For example, a HELO argument of over 10,000 characters may overflow the buffer, and a HELO argument of over 12,000 characters may even crash the server.
You might also like to view...
The market for m-commerce in North America is maturing much earlier than in Western Europe and Japan.
Answer the following statement true (T) or false (F)
How many and what kind of variables (primitive or object) are created in the code below?
> World worldObj = new World(); // worldObj is an object variable > Turtle turtle1 = new Turtle(worldObj); // turtle1 is an object variable > turtle1.forward(30); > Turtle turtle2 = new Turtle(worldObj); // turtle2 is an object variable > turtle2.turnRight(); > turtle2.forward(30);
Find the x- and y-intercepts of the equation and use them to sketch the graph. ![]()
A. 
x-intercept ![]() , y-intercept none
, y-intercept none
B. 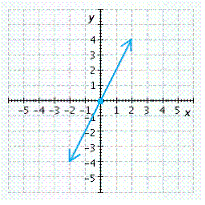
x-intercept ![]() , y-intercept
, y-intercept ![]()
C. 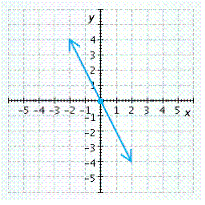
x-intercept ![]() , y-intercept
, y-intercept ![]()
D. 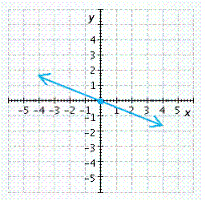
x-intercept ![]() , y-intercept
, y-intercept ![]()
E. 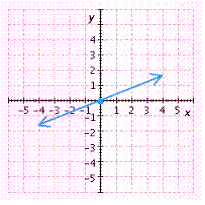
x-intercept ![]() , y-intercept
, y-intercept ![]()
Defense in Depth uses the military principle that it is more difficult for an enemy to defeat a complex and multi-layered defense system than to penetrate a single barrier.
a. true b. false