________ is a special tool that makes it easy to connect Excel to an Access database
A) Microsoft Query
B) Data connections
C) Excel Query
D) SQL Server
Answer: A
You might also like to view...
Who must be notified of Severity Level 3 incidents?
A) Chief Executive Officer B) Chief Operating Officer C) Chief Information Security Officer D) Legal counsel
Case-Based Critical Thinking QuestionsCase 13-1Lynn has to give a presentation in her public speaking class. The school has provided her with Microsoft PowerPoint, a popular presentation software. Lynn wants to make sure that her presentation is also fun to watch. She wants to use transition and animation effects to keep her audience interested. When using effects, Lynn should ____.
A. use as many effects as possible because they are fun and exciting to watch B. put sound effects on every slide to grab her audience's attention C. use a different transition on every slide and tell her audience which one she used in case they want to use them in their presentations D. use a few effects to jazz up her presentation, but not too many so as to irritate her audience
The following is a summary of the required tasks that are to be completed in this exercise:
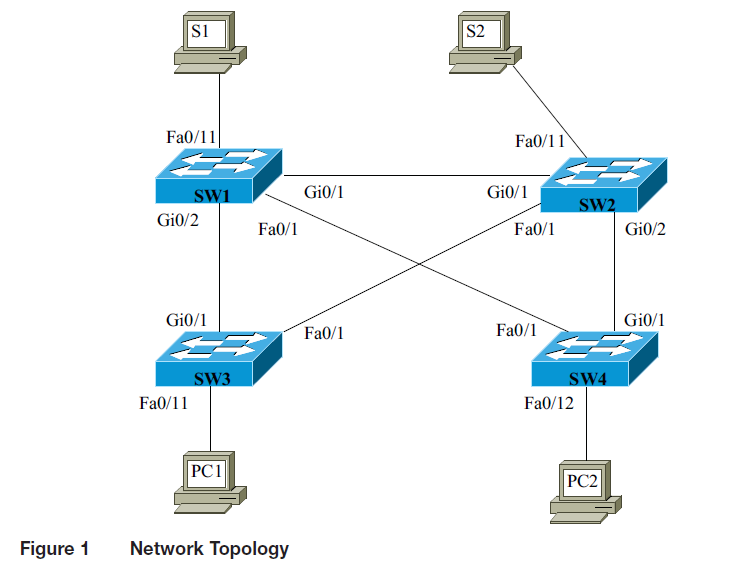
The objective of this project is to examine the student’s ability to configure VLANs using the
VLAN Trunking Protocol (VTP). VTP domain and passwords are up to the student. This network
setup uses four switches, with no redundant links. The network topology for this lab is provided in
Figure 1. The specific IP addresses are up to the student; however, they must be configured for
operation in the specified networks.
Specifics
? VLAN 10, Office: PC1, S2
? VLAN 20, Finance: PC2, S1
? Network: 192.168.10.0/24, 192.168.20.0/24
Disabled redundant ports:
? SW1(fa0/1), SW2(fa0/1), SW3(fa0/1), SW4(fa0/1)
VTP:
? VTP Server: SW1
? VTP Transparent: SW4
? VTP Clients: SW2, SW3
Required
1. Configure the network according to the specifications listed.
2. Disable the interfaces on any redundant links.
3. Configure the VTP server, clients, and transparent switch.
4. Add the VLANs to
When you click a hyperlink value, Access launches the appropriate program, such as a Web browser, Word, or Excel, and enables you to interact with the file.
Answer the following statement true (T) or false (F)