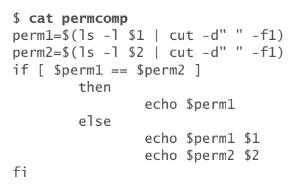
Write a short script that tells you whether the permissions for two files, whose names are given as arguments to the script, are identical. If the per- missions for the two files are identical, output the common permission field. Otherwise, output each filename followed by its permission field. (Hint: Try using the cut utility.)
What will be an ideal response?
You might also like to view...
____ sized arrays are not initialized with a set size, but instead are sized at execution to accommodate the listed values.
A. Statically B. Baseline C. Standard D. Implicitly
Most graphic intensive publications use ____ to standardize size and resolution of photos.
a. prefiguration b. color toning c. color isolation d. droplets
How can operational controls be used to improve security compliance?
A. Track activities with auditing and review the audit logs. B. Implement encryption and multifactor authentication. C. Set procedures for work tasks and provide training. D. Require M-of-N controls and place administrators into compartmented areas.
The Xpath 2.0 function _____ returns anxs:dateTimedata value based on anxs:date andxs:timevalue.
A. ?current-date() B. ?dateTime(date, time) C. ?day-from-date(date) D. ?current-dateTime()