A customer wants to leverage Amazon Simple Storage Service (S3) and Amazon Glacier as part of their backup and archive infrastructure. The customer plans to use third-party software to support this integration. Which approach will limit the access of the third party software to only the Amazon S3 bucket named "company-backup"?
A. A custom bucket policy limited to the Amazon S3 API in thee Amazon Glacier archive "company-backup"
B. A custom bucket policy limited to the Amazon S3 API in "company-backup"
C. A custom IAM user policy limited to the Amazon S3 API for the Amazon Glacier archive "company-backup".
D. A custom IAM user policy limited to the Amazon S3 API in "company-backup".
Answer: D. A custom IAM user policy limited to the Amazon S3 API in "company-backup".
You might also like to view...
Many association analysis algorithms rely on an Apriori-like approach for finding frequent patterns. The overall structure of the algorithm is given below.
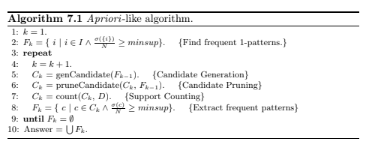
Suppose we are interested in finding boolean logical rules such as
{a ? b} ?? {c, d},
which may contain both disjunctions and conjunctions of items. The corre-
sponding itemset can be written as {(a ? b), c, d}.
(a) Does the Apriori principle still hold for such itemsets?
(b) How should the candidate generation step be modified to find such
patterns?
(c) How should the candidate pruning step be modified to find such pat-
terns?
(d) How should the support counting step be modified to find such pat-
terns?
Answer the following statements true (T) or false (F)
1. A solution is a group of related files, such as Visual Basic code, images and documentation. 2. Commands for managing the IDE and for developing, maintaining and executing programs are contained in the menus, which are located on the menu bar. 3. You can also access all the commands in the menus from the toolbar. 4. By clicking on the pluses (+) and minuses (-) in the node tree you can add or remove items. 5. Autohide is what enables the tool box to shrink down to the edge of the screen.
Entering the command _______________ at a Command Prompt will scan, detect, and repair hard drive volume- and sector-related issues.
Fill in the blank(s) with the appropriate word(s).
____________________ refers to the arrangement of data into tables and fields.
Fill in the blank(s) with the appropriate word(s).