An activity diagram for modeling the actions involved in executing a balance inquiry transaction using the BalanceInquiry object should not include:
a. Receiving the user’s main menu input selecting a balance inquiry transaction.
b. Retrieving the user’s balance information from the database of accounts.
c. Displaying the user’s balance information on the screen.
d. All of the above actions should be modeled in this activity diagram.
a. Receiving the user’s main menu input selecting a balance inquiry transaction.
You might also like to view...
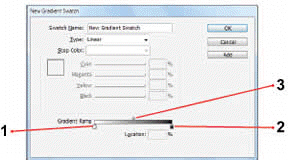 In the accompanying figure, which item is pointing to the diamond icon?
In the accompanying figure, which item is pointing to the diamond icon?
A. 1 B. 2 C. 3 D. none of the above
Using the P E R T diagram in Figure below determine the answers:
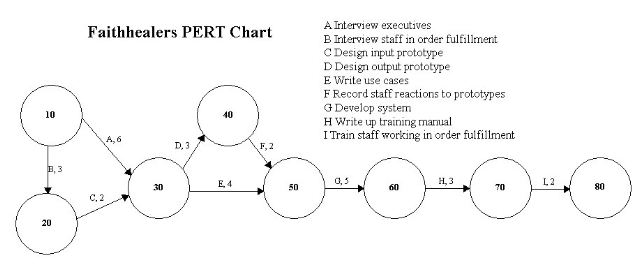
a. What activities can you expedite to complete the project a week ahead of schedule?
b. Suppose Activity E is the least costly activity to expedite. What happens if you try to expedite the project by more than one week? Explain.
Match the following Database Documenter Options with their descriptions:I.Include for table: permissions by User and GroupII.Include for Fields: Names, Data types, and SizesIII.Include for Fields: Names, Data types, Sizes, and propertiesIV.Include for Indexes: Names, Fields, and propertiesV.Include for table: propertiesA.Includes field names, data types, and field sizes for each field in the selected tablesB.Includes field names, data type, and field size for each field in the selected tables and options such as whether a zero-length value (or null value) is allowed, column width, and text alignmentC.Shows permissions for the tables based on users and/or groupsD.Documents table properties, including number of records, date of last update, and formattingE.Includes the names of all
indexes, the fields with which they are associated with, and the index properties, including the number of distinct index values and whether the index is required and must be unique Fill in the blank(s) with the appropriate word(s).
______ attacks are a variant of reflector attacks and also involve sending a packet with a spoofed source address for the target system to intermediaries.
Fill in the blank(s) with the appropriate word(s).