In which of the following attacks does an attacker install a fake communication tower between two authentic endpoints with the intention of misleading a user and interrupting the data transmission between the user and real tower to hijack an active session?
A. Rogue AP attack
B. Key reinstallation attack
C. Wardriving
D. aLTEr attack
Answer: D. aLTEr attack
You might also like to view...
Associated with each item in a data set is a special member that uniquely identifies the item in the data set.
Answer the following statement true (T) or false (F)
To display records for customers with incomes that are above $40,000 and below $70,000, use the ____________________ logical condition.?
Fill in the blank(s) with the appropriate word(s).
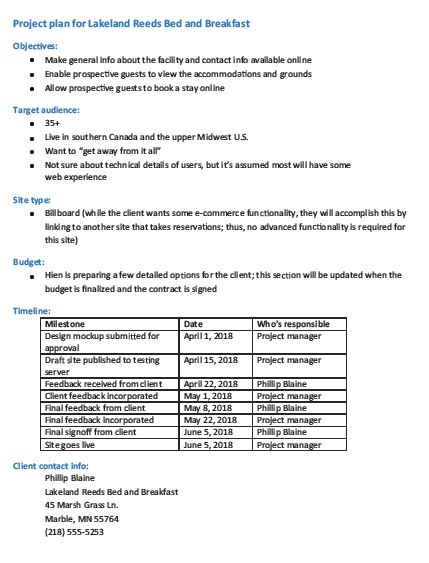
A. milestones B. completion date C. person responsible for each task D. None of the above, all of these items should be included
WiMax stands for ________.
A. wide-area access for maximum reach B. wide-area range to maximize access C. worldwide access to maximize interoperability D. worldwide interoperability for microwave access