What can a DHCP server do to enable active conflict detection?
What will be an ideal response?
The server can attempt to ping an IP address to ensure that an address isn't already in use before it is assigned.
You might also like to view...
Answer the following statements true (T) or false (F)
1. OS/JCL job names are always assigned by the operating system to eliminate the risk that two or more jobs might have the same name. 2. The job name, the operation (JOB), and accounting information are the only required fields on an OS/JCL JOB statement. 3. Accounting information is a positional parameter that (if present) is always the second parameter on an OS/JCL JOB statement. 4. Under OS/JCL, the meaning of a positional parameter is determined by its relative position in the operands field. 5. To simplify programmer identification, the programmer’s name, a required parameter, is coded as a second positional parameter on an OS/JCL JOB statement.
Configure switch 1 (sw1), router R1, PC1, PC2, and S1 using the IP addresses provided in Table 1. The IP addresses used in this exercise will all be configured as part of a 192.168.5.0 network.
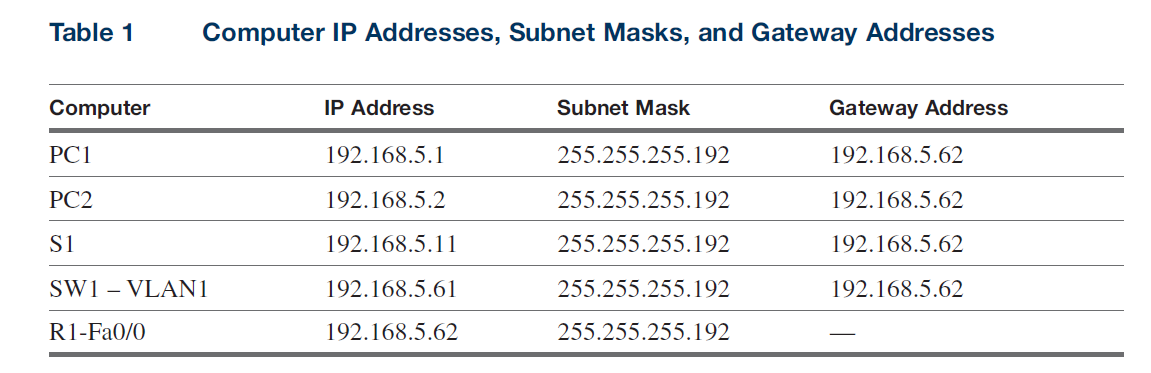
1. Your first task is to configure the switch SW1, the Router R1, the computers PC1 and PC2, and the switch S1 for the network provided in Figure 1. Use the IP addresses provided in Table 1.
2. After you have completed configuring the interfaces, verify that you have connectivity with all interfaces. List the commands used to verify network connectivity. Correct problems as needed.
3. Check whether port security has been enabled on the switch port connected to server S1 by using the show port-security interface Gi0/1 command. Record the status of the port security configuration on the interface based on the first line of output.
4. Configure port security using three commands: one command to make the port a statically configured access port, one command to enable port security, and one command to define the allowed MAC address, namely, S1’s MAC address of 0200.AAAA.AAAA. Record the three commands you used on the lines below.
5. Move back to enable mode and repeat the comman
What are the replies return by a trace?
What will be an ideal response?
Explain the difference between intrasite replication and intersite replication.
What will be an ideal response?