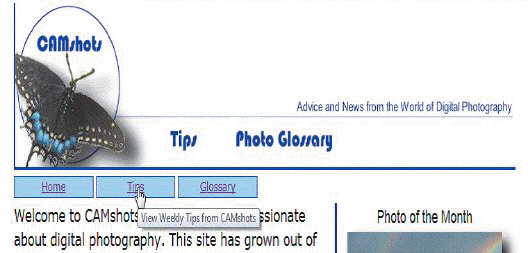
 The accompanying figure shows an example of a(n) ____ applied to a link.
The accompanying figure shows an example of a(n) ____ applied to a link.
A. access
B. tooltip
C. alternative
D. base
Answer: B
Computer Science & Information Technology
You might also like to view...
_____ is handy for files you want to back up or share while you are out and about.
A. Online storage B. Blu-ray disk C. Solid state drive D. Hard disk drive
Computer Science & Information Technology
All software, including public domain software, is protected by copyright.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
A(n) ________ is a network restricted to a small geographical area
Fill in the blank(s) with correct word
Computer Science & Information Technology
What should you be armed with to adequately assess potential weaknesses in each information asset?
A. properly classified inventory B. audited accounting spreadsheet C. intellectual property assessment D. list of known threats
Computer Science & Information Technology