Assumption of identity is the most common form of identity theft/fraud
Indicate whether the statement is true or false.
Answer: False
You might also like to view...
Every operating system contains a set of __________ routines that must be in memory at all times.
a. transient b. permanent c. resident d. kernel-based
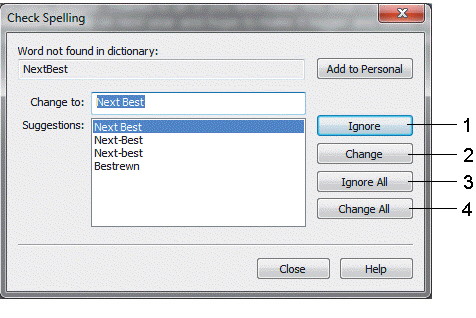 Click the item marked ____ in the accompanying figure to change a particular instance of a word to the selected correction.
Click the item marked ____ in the accompanying figure to change a particular instance of a word to the selected correction.
A. 1 B. 2 C. 3 D. 4
By default, only members of the Domain Admins and Group Policy Creator Owners groups have permissions to ________
a. Manage GPOs b. Create GPOs c. View GPOs d. None of the above
to protect users from each other,3. to protect users from themselves,4. to protect it from itself, and5. to protect itself from its environment. PTS: 1 2. What are the three security objectives of audit trails? Explain.
What will be an ideal response?