Using propaganda to influence opinions in a conflict is an example of which of the following?
A) Corporate espionage
B) Information warfare
C) Cyber terrorism
D) Hacktivism
B) Information war fare
Computer Science & Information Technology
You might also like to view...
Which of the following is used to associate a public key with an identity?
A) Encryption B) Digital hash C) Digital certificate D) Digital signature
Computer Science & Information Technology
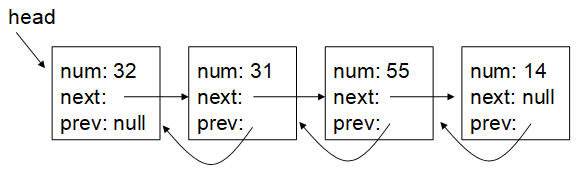
Given the doubly linked list in the diagram below, give the code to delete the second node in the list with the number 31. Assume each entry in the list is a node of class Node with a public next and prev member variable.
Computer Science & Information Technology
Why would you save search criteria as a saved search?
What will be an ideal response?
Computer Science & Information Technology
?

A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology