Which of the following cryptographic concepts has been widely discredited among the information security community?
a. Confidentiality
b. Nonrepudiation
c. Security though obscurity
d. Integrity
e. Authentication
Answer: c. Security though obscurity
You might also like to view...
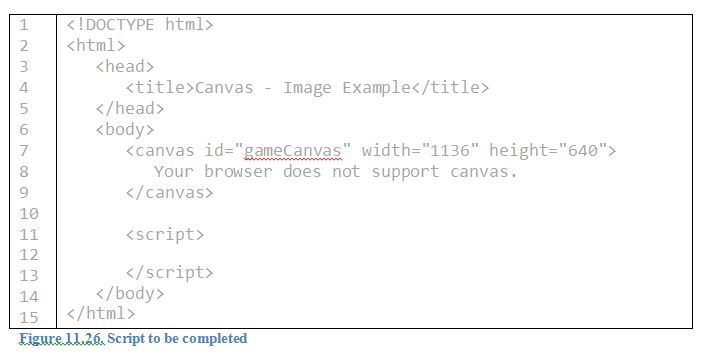
Place the following statements (a) - (d) in the correct order in line 12 of the code shown in Figure 11.26 so that a tree image will be displayed on the canvas.
a. myContext.drawImage(obstacle, 250, 70);
b. var myCanvas = document.getElementById("gameCanvas");
var myContext = myCanvas.getContext("2d");
c. obstacle.src = "images/tree.png";
d. var obstacle = new Image();
Some file properties can be user-modified with customized tags that describe and categorize files.
Answer the following statement true (T) or false (F)
The Bullets button is available on the Home tab of the ribbon in the ____ group.
A. Special Characters B. Format C. Paragraph D. Options
When a list provides individual data location capability, it becomes a(n) ____.
A. built-in list type B. advanced list C. data structure D. queue