A ________ can compromise the security of your data because it is easy to guess.
a. strong password
b. weak password
c. CAPTCHA
d. bot
Answer: b. weak password
You might also like to view...
The management of the development or service is itemized in which sections of the ISO 12207-2008 standard?
A. Implementation process group (7.1) B. Software-specific process domain (7.0) C. Validation and verification activities (7.2.5 and 7.2.4) D. Project-enabling and project process groups (6.2 and 6.3)
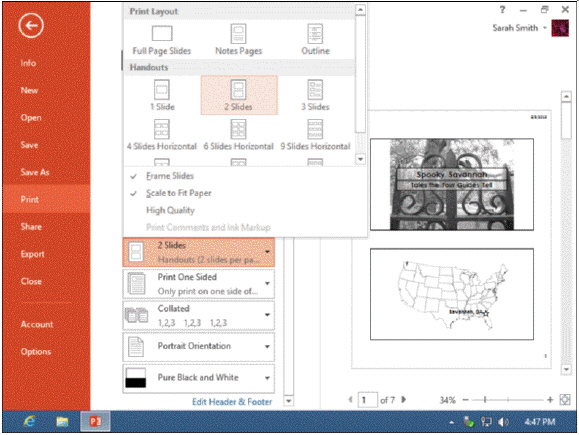 Referring to the accompanying figure, which of the following layouts prints blank lines to the right of each slide?
Referring to the accompanying figure, which of the following layouts prints blank lines to the right of each slide?
A. 3 slides B. 2 slides C. 4 slides D. 6 slides
Use the ______ attribute to display an image to the right of a block of text
a. align b. spacing c. alt d. height
Which of the following is used with Windows to secure data from unauthorized users?
A) REGEDIT B) Compression C) EFS D) Network Neighborhood