When building a table, you can set up a(n) ________ to restrict the data values that the user can enter into a field
Fill in the blank(s) with correct word
validation rule
You might also like to view...
The more layers in a file, the larger the file size, and therefore ____ layers is used to reduce file size.
A. consolidating B. merging C. flattening D. drafting
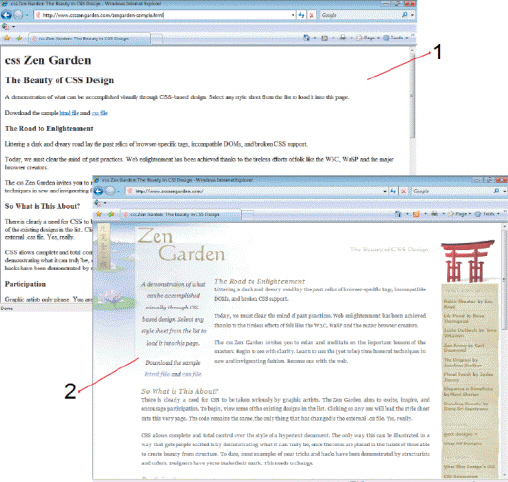 Referring to the figure above, Item ____ is pointing to a Web page with a style sheet applied.
Referring to the figure above, Item ____ is pointing to a Web page with a style sheet applied.
A. 1 B. 2
Julia encrypts a message to David using public key encryption for confidentiality. After encrypting the message, can Julia decrypt it?
True False
A user is trying to setup a small office home office (SOHO) wireless network and does not want any neighbors to be able to discover the network. Which of the following parameters would MOST likely be configured?
A. Configure a proxy server address B. Enable WEP encryption C. Disable SSID broadcast D. Configure DMZ settings