One form of software theft is the theft of the software from software manufacturers, which is known as piracy. Because this has historically been rather easy to do, the practice has become very common. As a computer instructor you feel it is your responsibility to explain this practice to students through the use of some examples.
?
Which of the following practice IS permissible under a single-user license agreement?
?
a. Ahmed rents his copy of Adobe Illustrator.b. The lab administrator at the college installs Fireworks on the school computer lab network.c. Karen installs Flash on one desktop computer and one notebook computer.d. Perry gives a copy of Microsoft Word 2013 to his friend, while continuing to use the software.
What will be an ideal response?
Answer: C
You might also like to view...
Python module________enables developers to access the shell to run other programs and control those programs’ input and output.
a) os. b) POSIX. c) osmod. d) None of the above.
What are the handles pointing to?
What will be an ideal response?
Step 1. Explore threads.
a. Open a command prompt.
b. In the Process Explorer window, right-click conhost.exe and Select Properties….. Click
the Threads tab to view the active threads for the conhost.exe process.
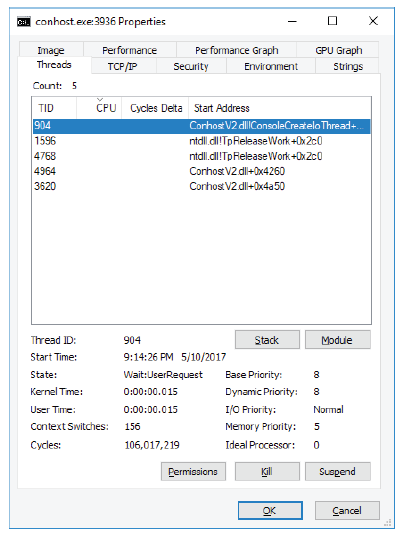
c. Examine the details of the thread.
Step 2. Explore handles.
In the Process Explorer, click View > select Show Lower Pane > Handles to view the handles
associated with the conhost.exe process.
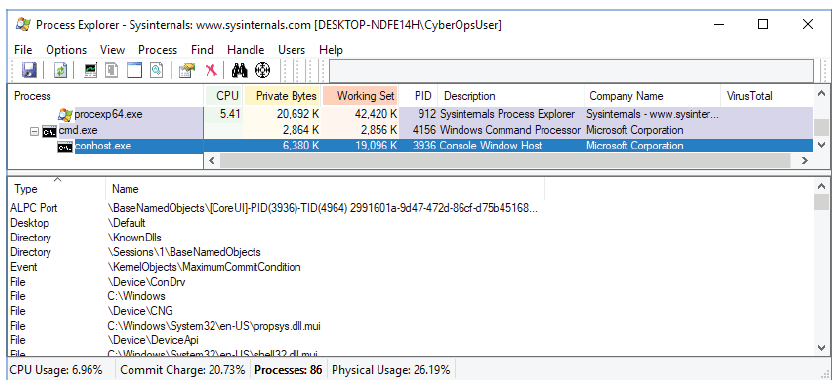
Examine the handles.
Where is a host-based IDPS agent typically placed?
A. on a workstation or server B. at Internet gateways C. between remote users and internal network D. between two subnets
Contacts to a support staff about security, viruses, backups, and ergonomics indicate ____________________.
Fill in the blank(s) with the appropriate word(s).