________ is the use of the Internet, smartphones, or other devices to send or post content intended to hurt or embarrass another person.
A. Identity theft
B. Trojan horse attack
C. Zombie apocalypse
D. Cyberbullying
Answer: D
Computer Science & Information Technology
You might also like to view...
Can you use the random_shuffle generic algorithm with a list container? What about a vector container? Why or why not?
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Explain the disadvantages of using magnetic storage media and what you should do to counteract these disadvantages.
What will be an ideal response?
Computer Science & Information Technology
How are you planning on depicting your player’s progress through the game?
What will be an ideal response?
Computer Science & Information Technology
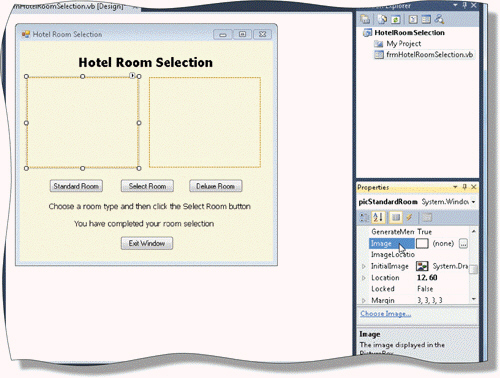 In the accompanying figure, clicking the Ellipsis button at the end of the Image property of the PictureBox object will display the ____ dialog box.
In the accompanying figure, clicking the Ellipsis button at the end of the Image property of the PictureBox object will display the ____ dialog box.
A. Visuals B. Select Resource C. Graphics D. Objects
Computer Science & Information Technology