The X.25 standard uses which protocol at the Frame Level?
a. V.24
b. LAP-B
c. X.3
d. none of the above
b. LAP-B
You might also like to view...
________ is the process of anticipating and controlling for errors
A) Debugging B) Error handling C) Event-driven programming D) Compiling
How is a speed transition created?
What will be an ideal response?
The purpose of a computer forensics investigator's report is to convey an opinion or convince a jury that a suspect is guilty, not detail findings
Indicate whether the statement is true or false.
Case 1Sam works as a Web designer for XYZ Corporation. He is creating an Interactive Button and starts by opening the Interactive Buttons dialog box shown in the figure below. 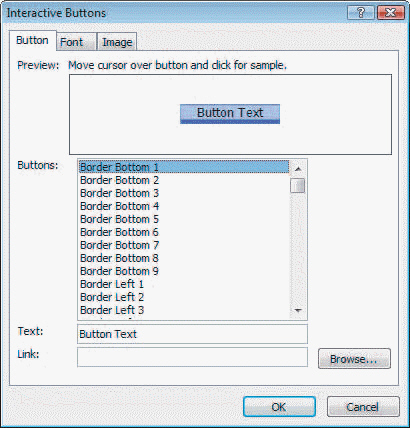 Referring to the figure above, when Sam points to the Preview area, the image changes to a preview of the button's ____ state.
Referring to the figure above, when Sam points to the Preview area, the image changes to a preview of the button's ____ state.
A. pressed B. hover C. original D. visited