Another term for search results is __________
a. hits
b. metadata
c. spider
A. hits
You might also like to view...
The system displays the following message when you attempt to log in with an incorrect username or an incorrect password:
Login incorrect a. This message does not indicate whether your username, your password, or both are invalid. Why does it not reveal this information? b. Why does the system wait for a couple of seconds to respond after you supply an incorrect username or password?
Describe DNS Security Extensions (DNSSEC).
What will be an ideal response?
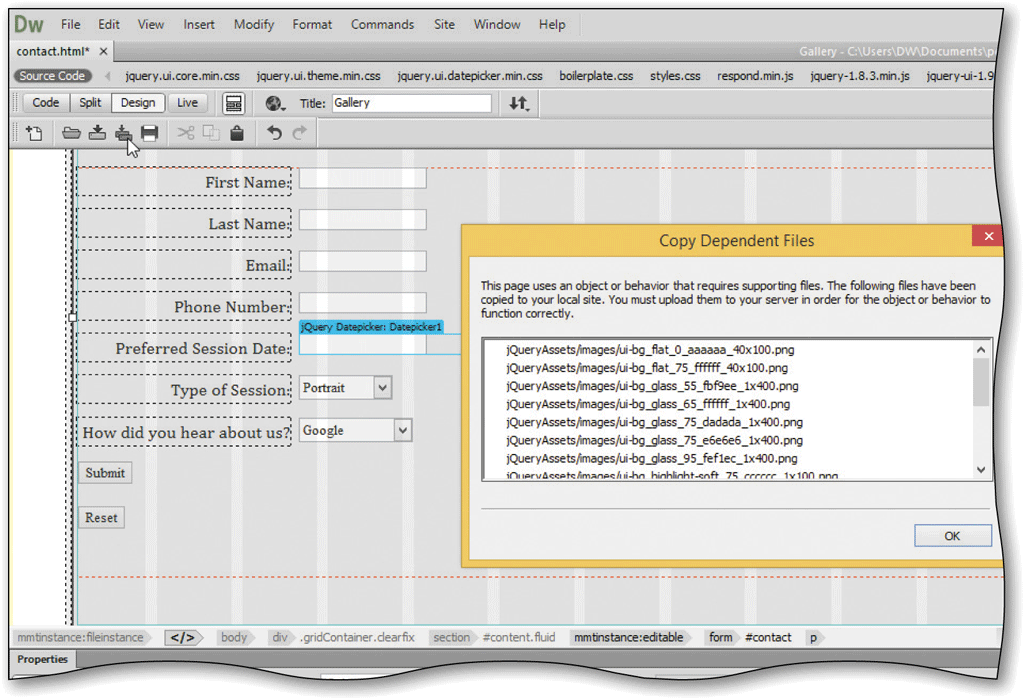
A. The user has inserted 8 new widgets at one time. B. jQuery UI widgets come with dependent files that must be copied in order to make the widget function. C. This is a legacy function of HTML4 and can be safely ignored in Dreamweaver CC. D. The user has chosen to create interactivity in HTML5 rather than using jQuery UI widgets.
What is an n-tier architecture?
What will be an ideal response?