All cell phones are examples of a personal computer.
Answer the following statement true (T) or false (F)
False
You might also like to view...
For each of the following types of data or clusters, discuss briefly if (1) sam- pling will cause problems for this approach and (2) what those problems are. Assume that the sampling technique randomly chooses points from the to- tal set of m points and that any unmentioned characteristics of the data or clusters are as optimal as possible. In other words, focus only on problems caused by the particular characteristic mentioned. Finally, assume that K is very much less than m.
Hierarchical clustering algorithms require O(m2 log(m)) time, and conse- quently, are impractical to use directly on larger data sets. One possible technique for reducing the time required is to sample the data set. For ex- ample, if K clusters are desired and ?m points are sampled from the m points, then a hierarchical clustering algorithm will produce a hierarchical clustering in roughly O(m) time. K clusters can be extracted from this hier- archical clustering by taking the clusters on the Kth level of the dendrogram. The remaining points can then be assigned to a cluster in linear time, by using various strategies. To give a specific example, the centroids of the K clusters can be computed, and then each of the m ? ?m remaining points can be assigned to the cluster associated with the closest centroid. (a) Data with very different sized clusters. (b) High-dimensional data. (c) Data with outliers, i.e., atypical points. (d) Data with highly irregular regions. (e) Data with globular clusters. (f) Data with widely different densities. (g) Data with a small percentage of noise points. (h) Non-Euclidean data. (i) Euclidean data. (j) Data with many and mixed attribute types.
FIGURE WD 4-1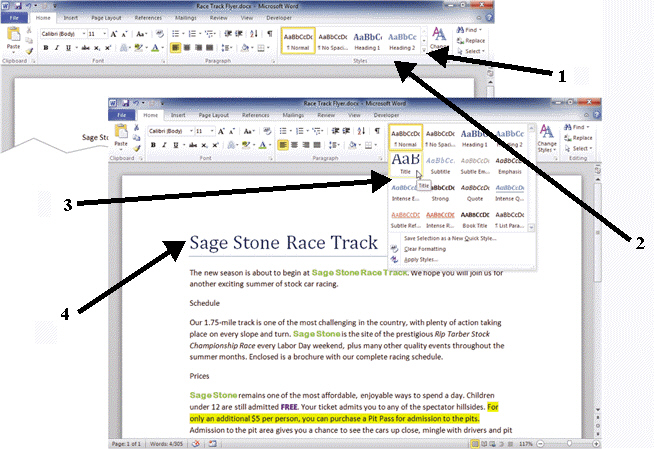 The item numbered 1 in Figure WD 4-1 above is the ____ button in the Styles group.
The item numbered 1 in Figure WD 4-1 above is the ____ button in the Styles group.
A. Styles B. Fonts C. More D. Preview
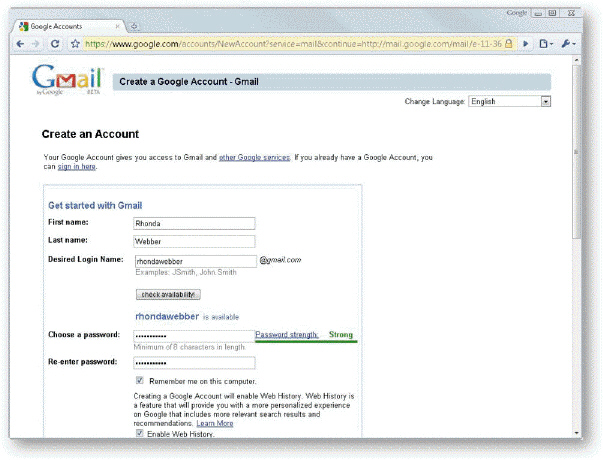 In the accompanying figure, ____ checks to make sure that the login name you want has not been claimed by another user.
In the accompanying figure, ____ checks to make sure that the login name you want has not been claimed by another user.
A. check availability B. perform checksum C. check digit D. check strength
?Hypertext organizes data through a series ofsitesusers can activate to jump from one piece of information to another.
Answer the following statement true (T) or false (F)