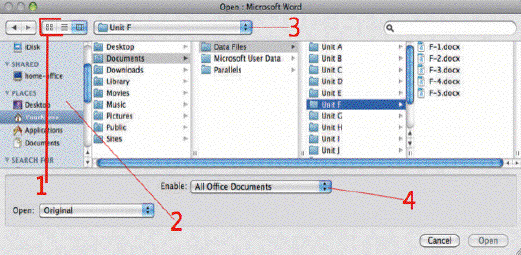
 In the accompanying figure, Item 2 points to the ____.
In the accompanying figure, Item 2 points to the ____.
A. program window
B. draft view
C. styles gallery
D. sidebar
Answer: D
Computer Science & Information Technology
You might also like to view...
Wireless security was implemented well in the original 802.11 standard.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
Briefly define proxy server, screening host, and screening router.
What will be an ideal response?
Computer Science & Information Technology
The Fourth Amendment of the U.S. Constitution _____.
a. protects the privacy of intermediate school students b. protects the privacy of college students c. protects the privacy of private employees d. protects the privacy of government employees
Computer Science & Information Technology
Describe the working of an effective electronic discovery (e-discovery) software solution.
What will be an ideal response?
Computer Science & Information Technology