________ is the destruction of hardware, software, or data.
A. Extortion
B. Hacking
C. Denial of Service
D. Sabotage
D. Sabotage
Computer Science & Information Technology
You might also like to view...
Explain the difference between RGB and CMYK color. What does it mean that one of them is additive and one is subtractive?
What will be an ideal response?
Computer Science & Information Technology
On switch SW3, what is the spanning tree information now? What is the STP path?
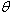
What will be an ideal response?
Computer Science & Information Technology
How does the Table Analyzer tool make you more productive?
What will be an ideal response?
Computer Science & Information Technology
What is design thinking used for?
What will be an ideal response?
Computer Science & Information Technology