A(n) ____________________ system contains pseudo-services that emulate well-known services, but is configured in ways that make it look vulnerable to attacks.
Fill in the blank(s) with the appropriate word(s).
honeypot
You might also like to view...
Each section in a document can have different headers and footers.?
Answer the following statement true (T) or false (F)
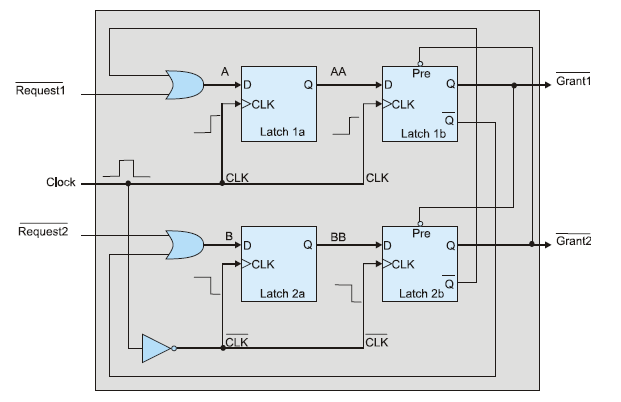
The clocked circuit below is an arbiter. Suppose two devices 1 and 2 can request a resource such as a bus at any instant. The problem is to ensure that only one requester is granted the resource, even if both requests are made simultaneously. The circuit of Figure P12.20 has two request inputs plus a clock and two grant outputs. Explain how the circuit is able to perform its function reliably. Note that the circuit uses edge?triggered flip?flops and that it is immune to metastablilty.
The primary need for a(n) _______________ workstation is a large, high-quality monitor.
Fill in the blank(s) with the appropriate word(s).
If you edit an original file, you should save it with a different filename.
Answer the following statement true (T) or false (F)