A(n) ____________________ gets its data for the zone from the master server for that zone.
Fill in the blank(s) with the appropriate word(s).
secondary DNS server
You might also like to view...
If a datagram has an incorrect value in one of the header fields, which ICMP error message will be received?
What will be an ideal response?
Configure the network routers (R1 and R2) and computers PC1 and PC2 to operate in the network using the IP addresses, subnet masks, and gateway addresses specified in Table 1. You are to also configure Routing Information Protocol (RIP) routing between the two networks.
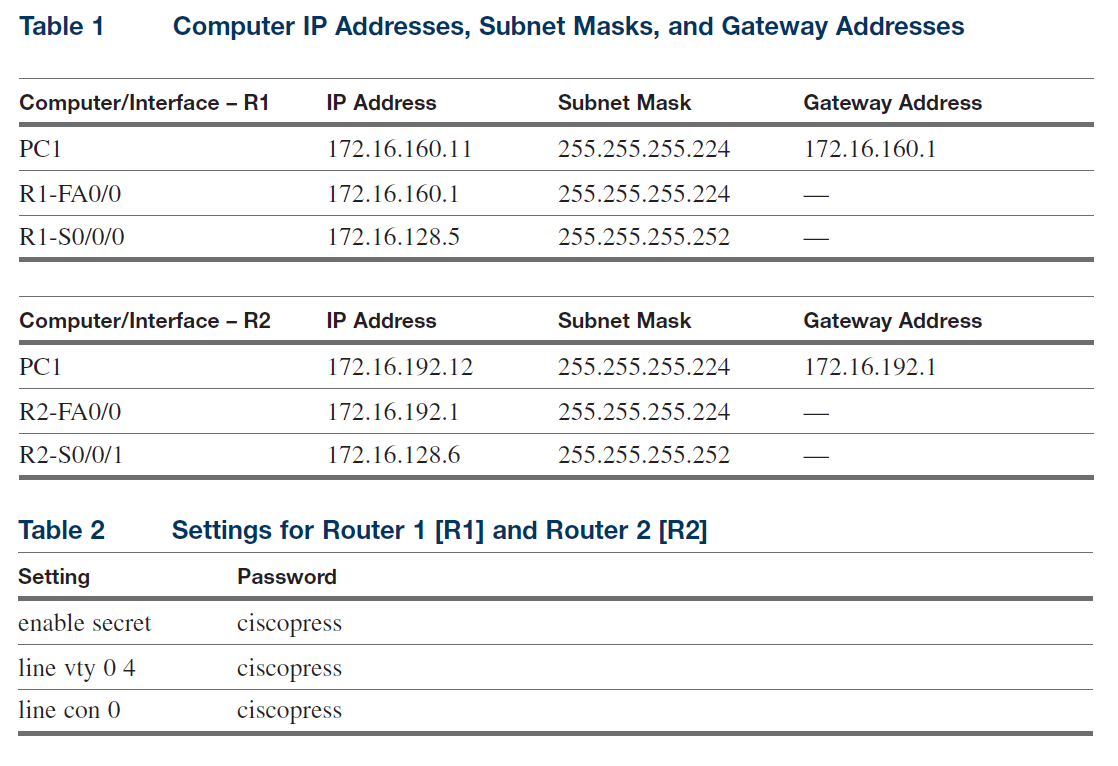
1. Configure the IP address and subnet masks for Routers R1 and R2 and PC1 and PC2. List the steps taken to accomplish this task. List the router prompts and commands for each task.
2. Configure RIPv2 routing for the network. List the router prompts and commands to accomplish this task.
3. Verify that the network routing is properly configured. Discuss the steps you took to accomplish this. Make corrections to the network configurations as needed.
4. In this step, you will create an ACL on Router R1 that filters all User Datagram Protocol (UDP) traffic coming into the serial 0/0/0 interface on Router R1. You will also allow all other traffic, including Internet Control Message Protocol (ICMP), to enter the network. You can simulate UDP traffic by issuing the traceroute command, and you can simulate ICMP traffic by issuing the ping command. Given this information, create an access list that meets this requirement. Note that when testing your access list you will issue the traceroute and ping commands from Router R2
Which of the following refers to the amount of horizontal space between characters?
A) Character spacing B) Scaling C) Kerning D) Position
Which role evaluates the security needs of the organization and develops the internal information security governance documents?
A. Security administrator B. Security analyst C. Data custodian D. Data owner