Configure the network routers (R1 and R2) and computers PC1 and PC2 to operate in the network using the IP addresses, subnet masks, and gateway addresses specified in Table 1. You are to also configure Routing Information Protocol (RIP) routing between the two networks.
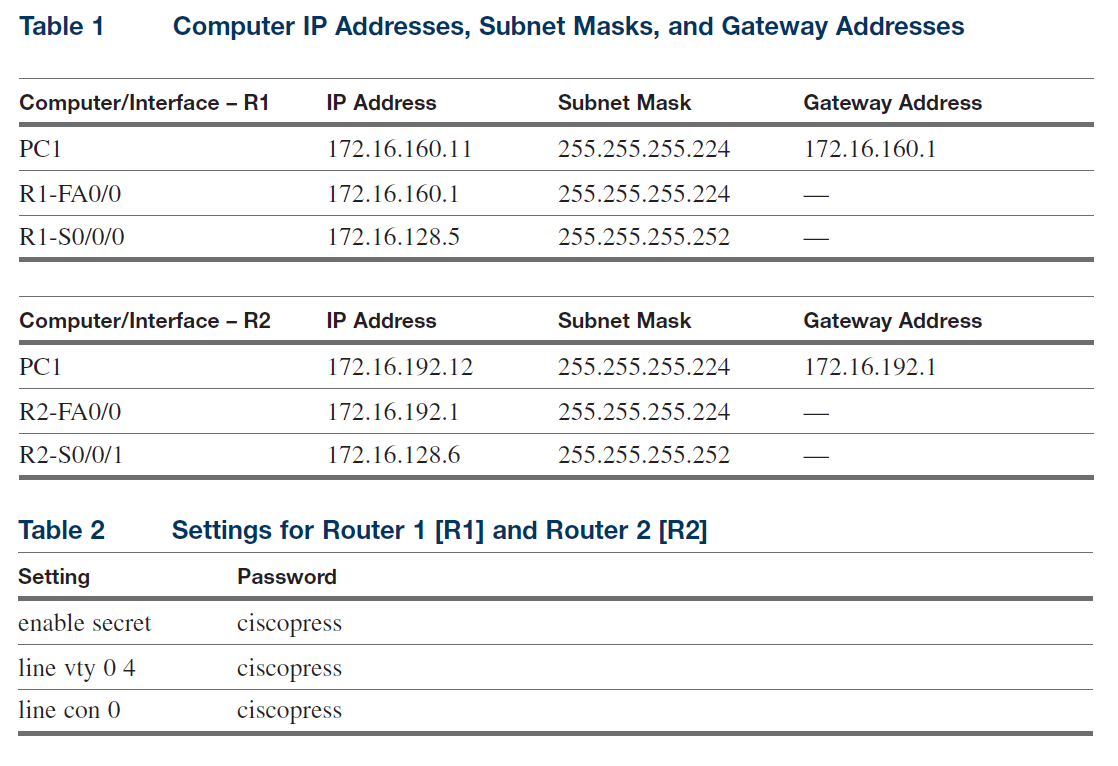
1. Configure the IP address and subnet masks for Routers R1 and R2 and PC1 and PC2. List the steps taken to accomplish this task. List the router prompts and commands for each task.
2. Configure RIPv2 routing for the network. List the router prompts and commands to accomplish this task.
3. Verify that the network routing is properly configured. Discuss the steps you took to accomplish this. Make corrections to the network configurations as needed.
4. In this step, you will create an ACL on Router R1 that filters all User Datagram Protocol (UDP) traffic coming into the serial 0/0/0 interface on Router R1. You will also allow all other traffic, including Internet Control Message Protocol (ICMP), to enter the network. You can simulate UDP traffic by issuing the traceroute command, and you can simulate ICMP traffic by issuing the ping command. Given this information, create an access list that meets this requirement. Note that when testing your access list you will issue the traceroute and ping commands from Router R2
1.
```
config-if)# ip address 172.16.160.1 255.255.255.224
R1(config-if)# no shut
R1(config-if)#
R1# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)# interface serial 0/0/0
R1(config-if)# ip address 172.16.128.5 255.255.255.252
R1(config-if)# clock rate 128000
R1(config-if)# no shut
R1(config-if)#
PC1
C:\> ip address 172.16.160.11 255.255.255.224
C:\> gateway 172.16.160.1
Router R2
R2# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)# int fa0/0
R2(config-if)# ip address 172.16.192.1 255.255.255.224
R2(config-if)# no shut
R2(config-if)#
R2# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)# interface s0/0/1
R2(config-if)# ip address 172.16.128.6 255.255.255.224
R2(config-if)# no shut
R2(config-if)#
PC2
C:\> ip address 172.16.192.12 255.255.255.224
C:\> gateway 172.16.192.1
```
2.
```
R1(config)# router rip
R1(config-router)# version 2
R1(config-router)# network 172.16.0.0
R1(config-router)#
R2(config)# router rip
R2(config-router)# version 2
R2(config-router)# network 172.16.0.0
R2(config-router)#
```
3.
```
R2# sh ip route
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 3 subnets, 2 masks
R 172.16.160.0/27 [120/1] via 172.16.128.5, 00:22:20, Serial0/0/1
C 172.16.128.4/30 is directly connected, Serial0/0/1
C 172.16.192.0/27 is directly connected, FastEthernet0/0
R2#
R1# sh ip route
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 3 subnets, 2 masks
C 172.16.160.0/27 is directly connected, FastEthernet0/0
C 172.16.128.4/30 is directly connected, Serial0/0/0
R 172.16.192.0/27 [120/1] via 172.16.128.6, 00:24:25, Serial0/0/0
R1#
Use the ping command to verify connectivity for Routers 1 and 2 and PC1 and PC2.
Also use sh ip int brief to verify interfaces. Next, verify the settings for PC1 and PC2.
The ping was successful from PC1 to PC2. No corrections needed. The show ip route
command shows that routing has been configured for all the networks.
```
4.
```
Create access list:
R1(config)# access-list 100 deny udp any any
R1(config)# access-list 100 permit ip any any
Apply access list to the s0/0/0 interface:
R1(config)# int s0/0/0
R1(config-if)# ip access-group 100 in
R2# ping 172.16.160.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.160.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round - trip min/avg/max =1/5/16 ms
R2# traceroute 172.16.160.1
Type escape sequence to abort.
Tracing the route to 172.16.160.1
1 * * *
2 * * *
3
R2#
```
5.
```
R1# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)# no access-list 100
R1(config)# line vty 0 4
R1(config-line)# password ciscopress
R1(config-line)# login
R1(config-line)#
Create access list:
R1(config)# access-list 100 deny tcp any any eq telnet
R1(config)# access-list 100 permit ip any any
R2#
R2# telnet 172.16.160.1
% Destination unreachable; gateway or host down
But the ping command still works to same interface.
R2# ping 172.16.160.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.160.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round - trip min/avg/max =1/5/16 ms
R2#
```
6,
```
R1(config)# no access-list 100
Create access list:
R2(config)# access-list 100 deny tcp 172.16.192.0 0.0.0.31 172.16.160.0
0.0.0.31 eq telnet
R2(config)# access-list 100 permit ip 172.16.192.0 0.0.0.31 172.16.160.0
0.0.0.31
Apply access list to the s0/0/1 interface:
R2(config)# int s0/0/1
R2(config-if)# ip access-group 100 in
```
You might also like to view...
Which of the following would NOT be true of the subject line?
A) should be left blank in informal messages B) should be descriptive of the message itself C) use of a descriptive message increases chances of message being opened D) contains a brief synopsis of the message
On some Web pages, information about downloads or blocked pop-up windows is commonly displayed on the ________
Fill in the blank(s) with correct word
Discuss the development of a data backup and recovery strategy and give an example.
What will be an ideal response?
When setting up an array, you need to instantiate an array object and assign it to the array declaration.
Answer the following statement true (T) or false (F)