Does a VPN use link encryption or end-to-end encryption? Justify your answer
What will be an ideal response?
A
VPN
is
point-?to-?point
encryption.
It
may
be
on
a
single
link,
or
it
may
tunnel
through
a
more
complex
network;
in
the
latter
case
it
resembles
end-?to-?end
encryption.
You might also like to view...
An abstract class is
A) one that has at least one pure virtual function. B) one that supports polymorphism. C) one that has all of its member functions declared private. D) one that has all of its member variables declared private. E) None of the above
In this questions, you will configure RIP V2 to the adjacent LANs, LAN-A to LAN-B, based on the network topology provided in Figure 1. You are to use the IP addresses provided in Table 1. You will be asked to verify that computers in your LAN can ping the neighbor LAN. You are configuring routing for both 10.10.12.0 and 10.10.30.0 networks. A subnet mask of 255.255.255.0 is being used. Note that a serial interface is being used to interconnect the LANs. Use 56000 for the clock rate on the serial link (DCE interface). The enable secret and line console 0 password should be set to ciscopress.
Table 1 Computer IP Addresses, Subnet Masks, and Gateway Addresses
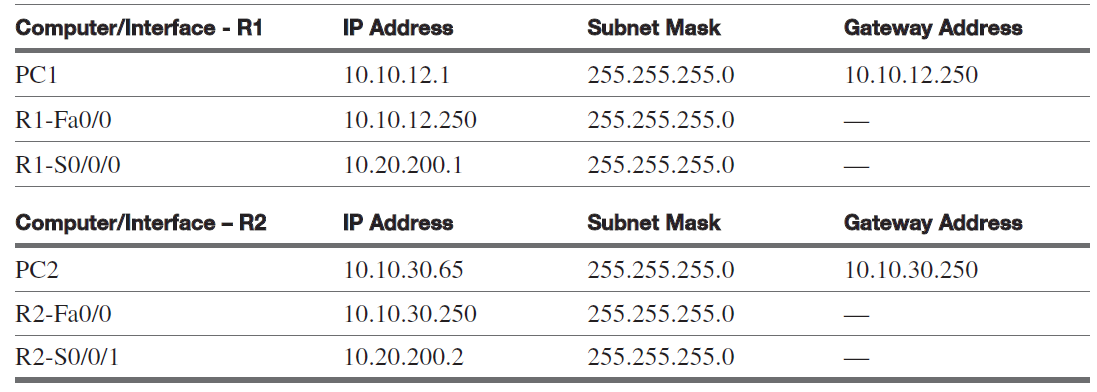
1. Configure the gateway address for your LAN routers according to the addresses listed in Table 1. List the prompts and the commands used to configure the gateway address and subnet mask on each of the routers.
2. Configure the host name for your routers; R1 should be renamed LAN-A and R2 should be renamed LAN-B. List the router prompts and commands used to configure the router’s host name.
3. Configure the routers' interfaces and include any relevant interface-specific commands and associated IP addresses and enable each of them; for this lab R1's S0/0/0 interface is the DCE with a rate of 56,000 kbps. Use the proper command to verify that the interfaces are properly configured. List the router prompts and commands used to accomplish this task.
4. Configure a RIP V2 route for both the LAN-A and LAN-B routers. Use two commands to verify that the routes are configured. List the router prompts and commands used to accomplish this.
To make lengthy text occupy more than one line in a cell, use the ________ button
A) Wrap Text B) Align Text C) Cell Height D) Break Text
Danny wants to print a form from a set of records in Microsoft Access 2016. He selects the records and clicks the Print button in the Print group on the Print Preview tab, which opens the Print Dialog box. Here, Danny notices that the option to _____ does not exist.?
A. ?print only selected records B. ?print all records C. ?print specified page numbers D. ?print selected number of copies