Julia encrypts a message to David using public key encryption for confidentiality. After encrypting the message, can Julia decrypt it?
True
False
False
You might also like to view...
Consider the Java code segment below:
``` Polygon poly2 = new Polygon(); poly2.addPoint(100, 30); poly2.addPoint(100, 130); ``` Which of the following will create a polygon that is a square? a. poly2.addPoint(100, 60); poly2.addPoint(100, 130); b. poly2.addPoint(200, 130); poly2.addPoint(200, 30); c. poly2.addPoint(200, 60); poly2.addPoint(200, 130); d. poly2.addPoint(100, 130); poly2.addPoint(100, 230);
A normal selector can be used to apply styles to several elements at one time
Indicate whether the statement is true or false
How is a speed transition created?
What will be an ideal response?
____ occurs when pixel values fall outside the range that can be reproduced in the color space in which you are working, as shown in the accompanying figure.
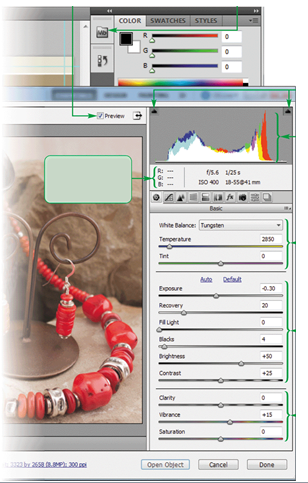
a. Saturation
b. Tonal adjustment
c. Clipping
d. White balance