?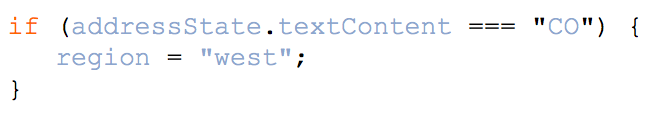
Referring to the figure above, the code in this figure creates a(n) __________.
A. function
B. ifstatement
C. variable
D. event listener
Answer: B
You might also like to view...
____ refers to the physical dimensions of the image.
A. File size B. Image size C. Image raster D. Image width
Policies are put in place to support the organization's mission, vision, and strategic planning.
Answer the following statement true (T) or false (F)
________ is a document view that displays how the document will look if all changes are accepted
Fill in the blank(s) with correct word
If an attacker decides to implement a less obvious port-scan, or stealth attack, which of the following techniques would be appropriate to make their activities more difficult to detect?
A. increase their scan speeds B. limit their tool set C. increase their scan speeds D. limit their scan speeds