IP spoofing
a. combines the messages of multiple users into a "spoofing packet" where the IP addresses are interchanged and the messages are then distributes randomly among the targeted users.
b. is a form of masquerading to gain unauthorized access to a web server.
c. is used to establish temporary connections between network devices with different IP addresses for the duration of a communication session.
d. is a temporary phenomenon that disrupts transaction processing. It will resolve itself when the primary computer completes processing its transaction and releases the IP address needed by other users.
B
You might also like to view...
In modern corporations-especially those in the United States and the United Kingdom-a primary objective of corporate governance is to ensure that the interests of top-level managers are aligned with the interests of shareholders.
Answer the following statement true (T) or false (F)
Marsh, Inc. provides the following information:
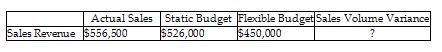
Calculate the sales volume variance.
A) 30,500 F
B) 30,500 U
C) $76,000 U
D) $106,500 F
Miguel’s job involves how the organization rewards the people who work for it. He works with salary surveys, benefits management, and incentive programs. Miguel’s human resource management specialty is ______.
A. the legal environment B. compensation and benefits C. safety and security D. ethics and sustainability
At one time Miller Beer was known as the "champagne of bottled beer." Unfortunately, Miller drinkers did not drink much beer. To increase sales, Miller was repositioned to attract the members of the middle working class
This segmentation approach is ________. A) user loyalty B) usage rate C) needs D) behavioral E) psychographic