A(n) _____ is a collection of tools, features, and interfaces that enables users to add, update, manage, access, and analyze data.
A. data logger framework
B. database management system
C. integrated development environment
D. advanced host controller system
Answer: B
You might also like to view...
What does the first pass of selection sort do?
a) Splits the array into two approximately equal pieces. b) Orders the first two elements of the array. c) Partitions the array into two unequal pieces depending on whether each element in the array is greater or less that some pivot element. d) Locates the smallest element in the array and swaps it into the zeroth position.
FCFS scheduling tends to result in an acceptable amount of ________ at the expense of ________.
a) throughput, fairness b) variance of response times, fairness c) variance of response times, throughput d) fairness, variance of response times
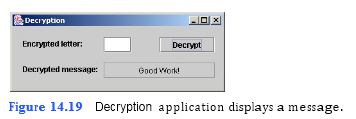
Develop an application that allows a user to decrypt a secret message (a string of numbers). The user should enter each number of the message one at a time in a JTextField. When the Decrypt JButton is clicked, the number should be decrypted to a letter. That letter should then be appended to the Decrypted message: JTextField. When the user enters the numbers 39, 79, 79, 68, 0, 55, 79, 82, 75, 1 in order, your application should appear as in Fig. 14.19.
a) Copying the template to your working directory. Copy the C:Exam- plesTutorial14ExercisesDecryption directory to your C:SimplyJava direc- tory.
b) Opening the template file. Open the Decryption.java file in your text editor.
c) Adding an instance variable. After the last GUI component is declared (line 18), add a declaration for a private String named message which will hold the decrypted message. Initialize message to the empty string. Use one line for a com- ment.
d) Storing the user input. Add code in the decryptJButtonActionPerformed method that will store the user input in an int variable named encryptedLetter. The rest of the code you will add in this exercises should be placed in the decryptJButtonAc- tionPerformed method.
e) Testing the user input. Your application should only accept user input in the range 0 to 94. Add an if statement that will test whether the user’s input is in the accepted range of values.
f) Decrypting the input. Add
Describe two examples of long-term storage devices.
What will be an ideal response?