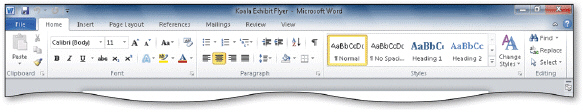
 The tool tabs in the accompanying figure are also called ____ tabs.
The tool tabs in the accompanying figure are also called ____ tabs.
A. contextual
B. dialog
C. shortcut
D. navigation
Answer: A
You might also like to view...
Show the first three merge steps done by merge sort for the following array. 9 18 51 39 15 45 14 5
What will be an ideal response?
A Widow occurs when the last line is split from the rest of the paragraph across a page break
Indicate whether the statement is true or false
An aggressive, intentional act carried out by a group or individual, using electronic forms of contact, repeatedly and over time against a victim who cannot easily defend him- or herself is known as ________
Fill in the blank(s) with the appropriate word(s).
Which of the following access control methodologies provides an individual with the most restrictive access rights to successfully perform their authorized duties?
A. Mandatory Access Control B. Rule Based Access Control C. Least Privilege D. Implicit Deny E. Separation of Duties