A(n) ______ is a potentially damaging program that affects, or infects, a computer or mobile device negatively by altering the way the computer or device works without the user's knowledge or permission.
Fill in the blank(s) with the appropriate word(s).
virus
You might also like to view...
Discuss the functionality and importance of the Integrity Enhancement Feature (IEF).
What will be an ideal response?
What is the keyboard shortcut for releasing an element from the master page, so that you can edit it on the document page?
What will be an ideal response?
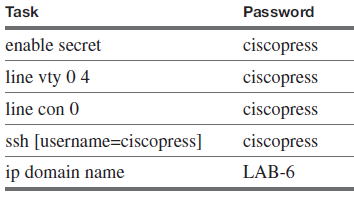
Configure the network according to the following specifications. You are to configure Enhanced IGRP (EIGRP) routing for the entire network. Use an autonomous system number of 100 for all EIGRP routing. Set the clock rate for all serial connections to 128 kbps. You are also to configure and enable the vty and console interfaces and provide ssh connections into and out of all routers.
Table 1 IP Addresses and Subnet Mask Requirements
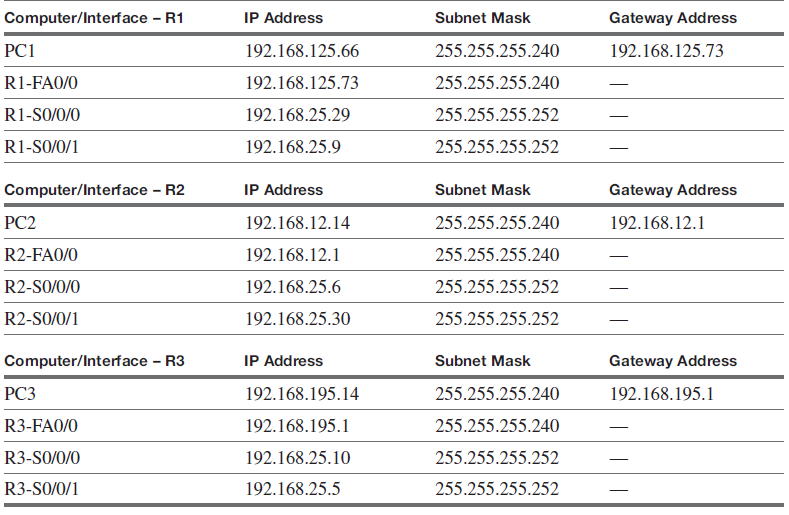
Table 2 Settings for R1, R2, R3
Jane has left the company. Her user account is a member of several groups and has permissions and rights to a number of forest-wide resources. Jane's replacement will arrive in a couple of weeks and needs access to the same resources. What's the best course of action?
a: Find all groups Jane is a member of and make note of the,. Delete Jane's user account and create a new account for the new employee. Add the new account to all the groups Jane was a member of. b: Copy Jane's user account and give the copy another name. c: Disable Jane's account. When the new employeee arrives, rename Jane's account, assign it a new password and enable it again. d: Export Jane's account and then import it when the new employee arrives. Rena,e the account and assign it a new password.