Which of the following is not one of the three types of security testing?
a. High-level assessments
b. Low-level assessments
c. Network evaluations
d. Penetration tests
ANS: B
You might also like to view...
In an application that uses declarative demarcation, one procedure that is called frequently from other procedures is a logging procedure that writes appropriate information about the state of the system into a log. What transaction attribute should be used for that procedure?
What will be an ideal response?
How can you be sure that data loaded with a URLRequest instance is available in Flash?
What will be an ideal response?
In the accompanying figureofa Microsoft Access 2016 document, the symbol that Box 1 is pointing to appears when you:?
?
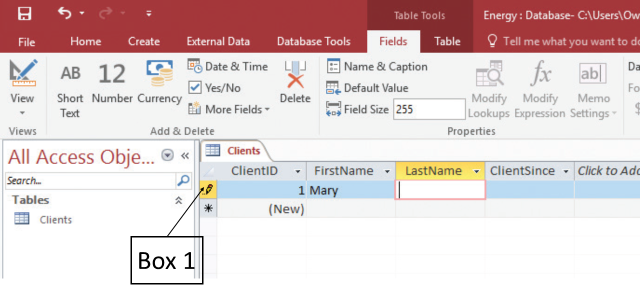
A. ?select the primary key value. B. ?delete a record. C. ?start typing a value in a field. D. ?modify the foreign key value.
The default setting for saving AutoRecover information is every ____ minutes.
A. 5 B. 10 C. 30 D. 60