A program's main module occupies a designated place in memory called the ____.
A. branch
B. stub
C. stack
D. base
Answer: C
You might also like to view...
Will your game benefit from in-game elements such as power-ups? Why or why not?
What will be an ideal response?
When using the Bing Image Search box, you can find various images that can be used under ________, which allows users to share and use their photos as long as the author is not profiting by selling the images
A) Microsoft Licensing B) Intellectual Property C) Free Information Act D) Creative Commons
FIGURE 10-1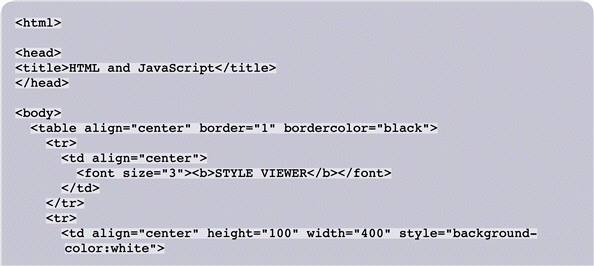
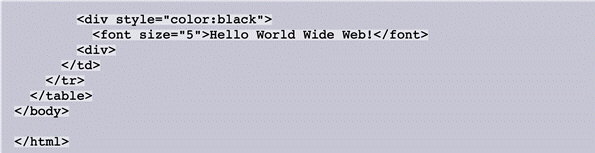 Referring to Figure 10-1 above, the style attribute of the second table cell initially sets the background color to ____.
Referring to Figure 10-1 above, the style attribute of the second table cell initially sets the background color to ____.
A. white B. black C. either a. or b. D. neither a. nor b.
The managerial tutorial equivalent of NIST SP 800-12, providing overviews of the roles and responsibilities of a security manager in the development, administration, and improvement of a security program, is NIST __________.
A. SP 800-100: Information Security Handbook: A Guide for Managers (2007) B. SP 800-18, Rev. 1: Guide for Developing Security Plans for Federal Information Systems (2006) C. SP 800-14: Generally Accepted Principles and Practices for Securing Information Technology Systems (1996) D. SP 800-110, Rev. 1: Manager's Introduction to Information Security (2016)