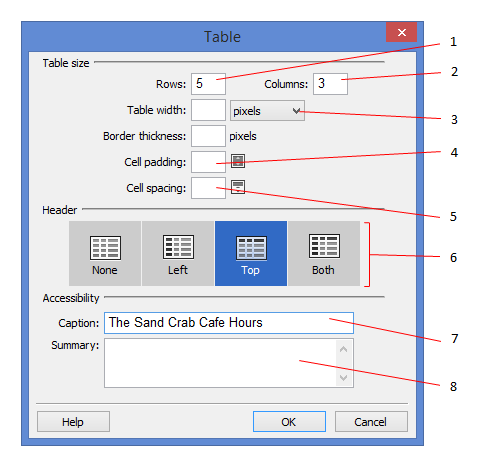
The figure above is a view of the ____________________ dialog box.
Fill in the blank(s) with the appropriate word(s).
Table
Computer Science & Information Technology
You might also like to view...
Which of the following key information security principles traces actions to their source?
A) Accountability B) Assurance C) Authorization D) Accounting
Computer Science & Information Technology
____ represent applications, storage areas, and links to social media sites.
A. Charm icons B. Start screen tiles C. Search features D. Desktop files
Computer Science & Information Technology
What is Default page?
What will be an ideal response?
Computer Science & Information Technology
Explain what the Buttons common library is and how it is used.
What will be an ideal response?
Computer Science & Information Technology