When peer-to-peer networks first appeared roughly 30 years ago, they were serverless networks.?
Answer the following statement true (T) or false (F)
True
You might also like to view...
A comment will include the user name and the time it was created
Indicate whether the statement is true or false
FIGURE AC 4-1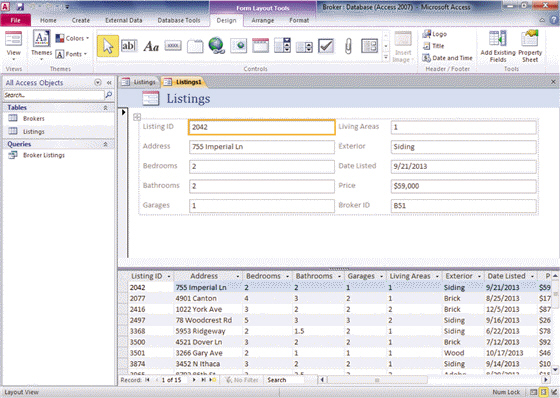 Referring to Figure AC 4-1 above, the form shown was created by using the ____ tool.
Referring to Figure AC 4-1 above, the form shown was created by using the ____ tool.
A. Double Form B. Double View C. Split Form D. Split View
What is the prime objective of code signing?
A. To verify the author and integrity of downloadable code that is signed using a public key B. To verify the author and integrity of downloadable code that is signed using a symmetric key C. To verify the author and integrity of downloadable code that is signed using a master key D. To verify the author and integrity of downloadable code that is signed using a private key
Vandalism is a type of human security threat.
a. true b. false