Which of the following are more secure file transfer alternatives to using FTP? (Select TWO).
A. SFTP
B. HTTP
C. SNTP
D. RCP
E. SCP
Answer:
A. SFTP
E. SCP
You might also like to view...
The getBooleanFromUser(prompt) function can be used with an if or while statement.
Answer the following statement true (T) or false (F)
The ________ thread should be used to perform all tasks that manipulate GUI components, because they are not thread safe.
a. event-handling b. event-dispatch c. GUI-handling d. None of the above.
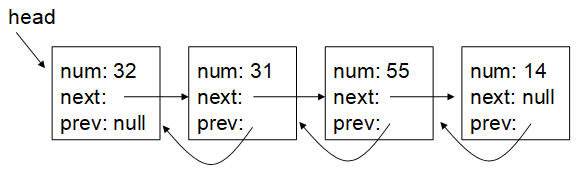
Given the doubly linked list in the diagram below, give the code to delete the second node in the list with the number 31. Assume each entry in the list is a node of class Node with a public next and prev member variable.
Case 17-2 Alisha, a teacher, is required to maintain a database of the students in her class. She keeps track of each student's name, registration number, grades, and the number of courses they have signed up for. She uses Microsoft Access 2016 to maintain and manage the database.? Alisha creates a report based on a table she created. The current database view does not display the number of pages included in the report. To view the number of pages in the report, she should switch to _____.
A. ?Outline Preview B. Design view? C. ?Print Preview D. ?Layout view