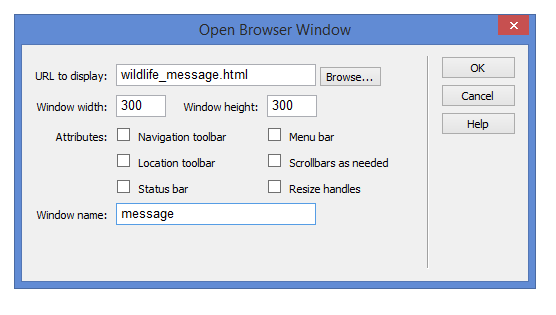
The figure above is the Behaviors dialog box.
Answer the following statement true (T) or false (F)
False
Computer Science & Information Technology
You might also like to view...
With the overflow property, ____ is the default value.
A. visible B. hidden C. scroll D. auto
Computer Science & Information Technology
Which of the following type of hackers hacks into systems to cause harm or steal data?
a. White hat b. Gray hat c. Green hat d. Black hat
Computer Science & Information Technology
Figure PPT 4-1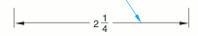 Which chart element is the red arrow pointing to in the accompanying figure?
Which chart element is the red arrow pointing to in the accompanying figure?
A. Chart title B. Horizontal axis title C. Vertical axis title D. Legend
Computer Science & Information Technology
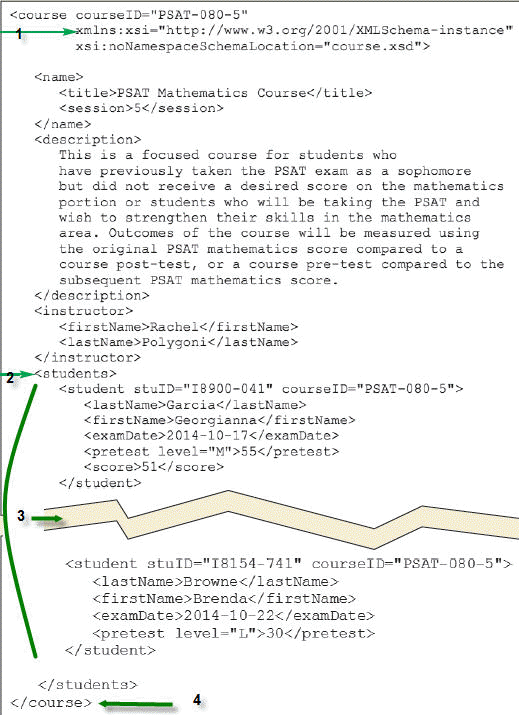
A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology