Individuals who purchase a Mac cite some key advantages of owning these types of computers. List and briefly describe these advantages.
What will be an ideal response?
(1) Mac computers seem to be more stable and suffer from fewer issues than PCs. (2) Macs rarely get infected by computer viruses and other malicious programs. (3) OS X includes various applications that a wide-range of individuals find very useful. (4) Apple's various devices work well with each other and all of your data is seamlessly synchronized to the cloud using Apple's iCloud service. (5) Excellent customer support, especially at Apple's stores. (6) You can run Windows on a Mac computer.
You might also like to view...
Write the code to declare an array of 10 doubles named list;
Fill in the blank(s) with the appropriate word(s).
Which of the following statements describes a legitimate source of the malicious data?
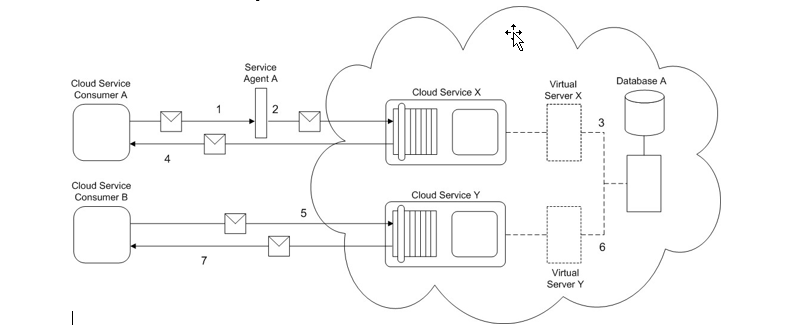
Cloud Service Consumer A sends a message to Cloud Service X (1), but it is first intercepted by Service Agent A (2) before actually being forwarded to Cloud Service X. Cloud Service X is hosted on Virtual Server X. Whenever an IT resource on Virtual Server X is accessed, the physical server that hosts Virtual Server X writes a log entry into Database A. After processing the request, Cloud Service X replies to Service Consumer A with a response message (4).
Cloud Service Consumer B sends a message to Cloud Service Y (5), which is hosted by Virtual Server Y. This virtual server is hosted by the same physical server as Virtual Server X and therefore when Cloud Service Y is accessed, a log entry is again written into Database A (6). After processing the request, Cloud Service X replies to Service Consumer A with a response message (7).
After being in use for several weeks, Cloud Service Consumer B unexpectedly shuts down. An investigation reveals that a response message sent by Cloud Service Y contained malicious data that
If an error is made entering a formula, the Enter key can be pressed to remove the contents and start over
Indicate whether the statement is true or false.
The ____ provides convenient, one-tap or one-click access to frequently used commands.
A. KeyTips toolbar B. Quick Access Toolbar C. mini toolbar D. Microsoft Account Area