Protecting a workbook encrypts it for internet transmission
Indicate whether the statement is true or false
FALSE
You might also like to view...
Identify valid variable names for the following, and state why the invalid names are not allowed.
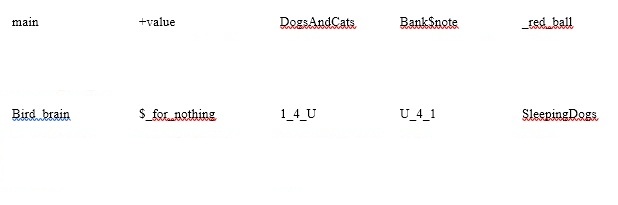
In two paragraphs, suggest a P C-based approach for capturing the elements of FOLKLORE so that it is not necessary to use a paper-based log. Make sure that your suggested solution can accommodate graphics as well as text.
What will be an ideal response?
The ____ lets you create high-quality images by choosing the percentage contribution from each color channel.
a. Channel Regulator b. Contribution Panel c. Channel Control d. Channel Mixer
Most of the connections that make up the high-speed backbone of the Internet use technologies designed at least 20 years ago to support telephone calls.
Answer the following statement true (T) or false (F)