_____ is the complete malfunction of a computer.
A. ?System failure
B. ?Shunt malfunction
C. ?Remote failure
D. ?System interruption
Answer: A
Computer Science & Information Technology
You might also like to view...
A __________ attack is where the source station specifies the route that a packet should take as it crosses the Internet in the hopes that this will bypass security measures that do not analyze the source routing information.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
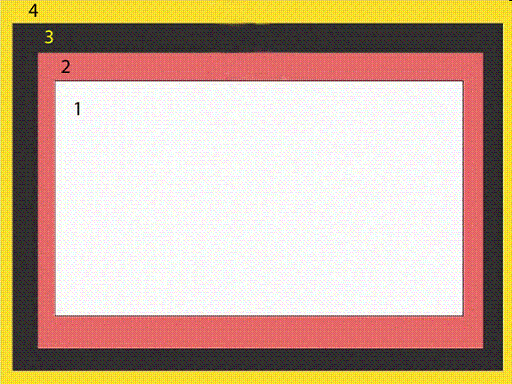 In the accompanying figure, the item marked 4 represents the ____.
In the accompanying figure, the item marked 4 represents the ____.
A. margin B. border C. content D. padding
Computer Science & Information Technology
The actual cells that a(n) ________ macro references will affect are not determined until the macro is run
Fill in the blank(s) with correct word
Computer Science & Information Technology
____ is a passive method of receiving WLAN signals.
A. CDMA B. RFMON C. SDIO NOW! D. Sled
Computer Science & Information Technology