Which of the following multifactor authentication technologies provides both low management overhead and flexibility?
A. Biometrics
B. Software tokens
C. Synchronous hardware tokens
D. Asynchronous hardware tokens
Answer: B. Software tokens
You might also like to view...
Case-Based Critical Thinking QuestionsCase 10-2Terrance had added a form to his blog to allow people to e-mail him feedback. He is having trouble getting his pages to validate and his JavaScript to work. Terrance's wants to document his code so others can understand his code. To document his JavaScript, he can use ____.
A. headers B. footers C. hidden boxes D. comments
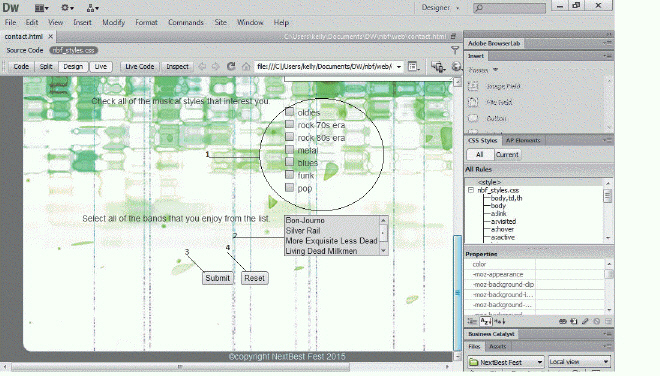 In a form like the one in the accompanying figure, a group of selection objects that work together in a form and that cannot be toggled independently of one another are known as ____ buttons.
In a form like the one in the accompanying figure, a group of selection objects that work together in a form and that cannot be toggled independently of one another are known as ____ buttons.
A. form B. radio C. check D. key
After adding a picture as a background, slide text will always be easier to read due to the contrast between the font and the background image
Indicate whether the statement is true or false
Define CIDR, including the full name for this acronym and why it is used.
What will be an ideal response?