___________ hat hackers break into other people's computer systems and may just look around or may steal and destroy information.
Fill in the blank(s) with the appropriate word(s).
Black
You might also like to view...
Which of the following is not the way U.S. auto mass producers operate?
A) greater labor content B) less mechanization C) less flexible mechanization D) divide employees in discrete specialties E) lack of employee teamwork
Which of the following is not true of accounting principles?
A) Financial accountants follow generally accepted accounting principles (GAAP). B) Following GAAP allows accounting information users to compare one company to another. C) A new accounting principle can be adopted with stockholders approval. D) The Financial Accounting Standards Board (FASB) has primary responsibility for developing accounting principles. E) Accounting principles develop from research, accepted accounting practices, and pronouncements of authoritative bodies.
Consider the portion of the sensitivity analysis report that follows. The current optimal solution will not change as long as the objective coefficient of X1 is within the range of ______.
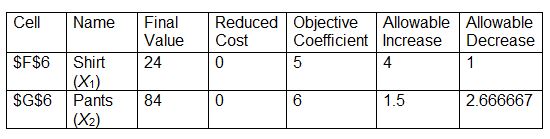
A. 4–9
B. 1–4
C. 5–9
D. 3–6
Nonlinear integer programming models offer additional challenges for solution algorithms because the values of Lagrange multipliers are valid only at the point of the optimal solution
a. True b. False