____ decides who should be trusted.
A. Logical security
B. Virtual security
C. Physical security
D. Personnel security
Answer: D
You might also like to view...
The Short Text data type is used for fields that contain words and symbols of up to _____ characters in length.
A. 128 B. 256 C. 255 D. 64
Configure the network according to the specifications listed. Make sure that you address both the router and switch access rules. Test your network carefully and then save your configuration.
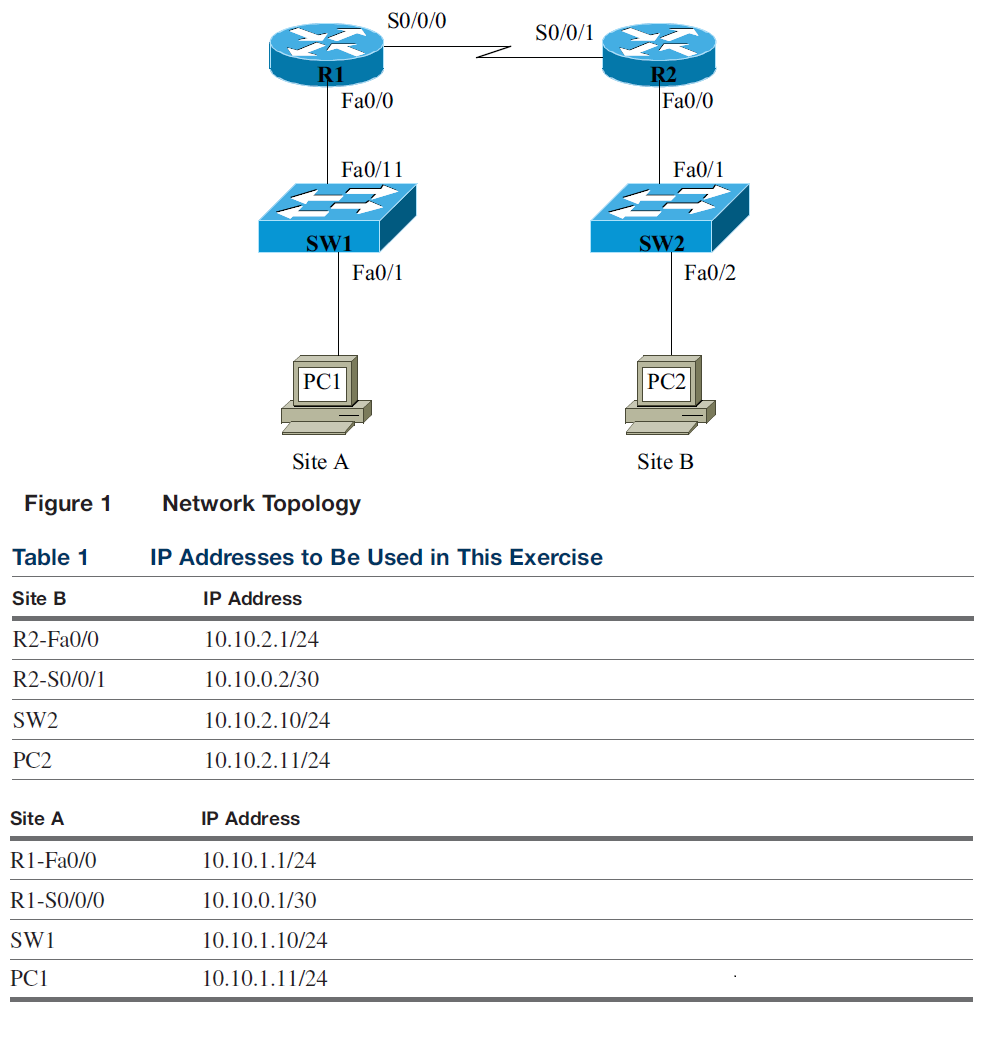
Specifics
Router access rules:
? Only computers in Site A are allowed to configure R1.
? Only computers in Site B are allowed to configure R2.
? Access to routers is restricted to use of the console port and Secure Shell (SSH) (use Telnet if
SSH is unavailable).
? All unused ports should be shut down.
Switch access rules:
? Only computers in Site A are allowed to configure SW1.
? Only computers in Site B are allowed to configure SW2.
? Access to switches is restricted to use of the console port and SSH (use Telnet if SSH is
unavailable).
? Use MAC address–based port security to ensure that only authorized devices can communicate.
? All unused ports should be shut down.
How is RF power measured using a relative scale?
What will be an ideal response?
A(n) __________ runs on a computer and approximates the dimensions and behavior of a wide range of devices.
Fill in the blank(s) with the appropriate word(s).